What is Cryptolocker?
Cryptolocker is initial version of ransomware-type virus. Although, this malware is no longer active, there are bunch of viruses based on it. And it’s no wonder why it motivated criminals to create similar projects. According to developers, their product got more than three million dollars from users who paid ransom. Today, we’ll consider one copycat form of it – Crypt0L0cker (TorrentLocker). Some newer variants even use initial name pretending to be original Cryptolocker ransomware. Following infiltration, it prevents access to your data using RSA-2048 encryption algorithm. All encrypted files are appended with .encrypted or .enc extensions. Then, 2 files, containing ransom message, will be created (DECRYTP_INSTRUCTIONS.html and DECRYPT_INSTRUCTIONS.txt). Unlike the old variant, the new one adds 6 random letters to extension of encrypted files, reinforcing all this by following files – HOW_TO_RESTORE_FILES.txt and HOW_TO_RESTORE_FILES.html.
DECRYTP_INSTRUCTIONS.html contains:
!!! WE HAVE ENCRYTPED YOUR FILES WITH Crypt0L0cker VIRUS !!!
What happened to my files? Your important files: photos, videos, document, etc. were encrypted with our Crypt0L0cker virus. This virus uses very strong encryption algorithm – RSA -2048. Breaking of RSA-2048 encryption algorithm is impossible without special decryption key. How can I get my files back? Your files are now unusable and unreadable, you can verify it by trying to open them. The only way to restore them to a normal condition is to use our special decryption software. You can buy this decryption software on our website.
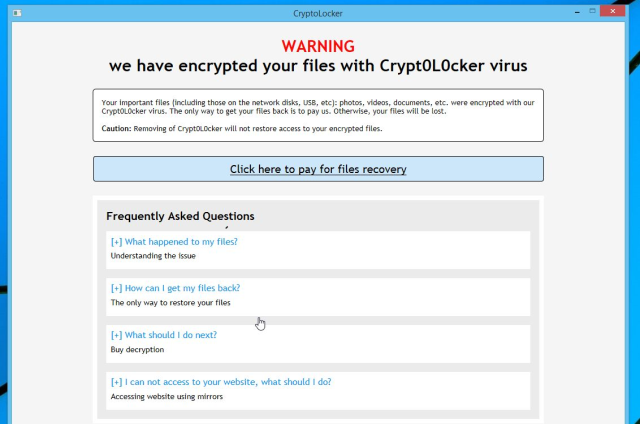
HOW_TO_RESTORE_FILES.html contains:
WARNING
we have encrypted your files with Crypt0L0cker virus
Your important files (including those on the network disks, USB, etc): photos, videos, documents, etc. were encrypted with our Crypt0L0cker virus. The only way to get your files back is to pay us. Otherwise, your files will be lost.
Caution: Removing of Crypt0L0cker will not restore access to your encrypted files.
To recover your files you have to pay.
In order to restore the files open our website – and follow the instructions.
If the website is not available please follow these steps:
1. Download and install TOR-browser from this link: https://www.torproject.org/download/download-easy.html.en
2. After installation run the browser and enter the address: –
3. Follow the instructions on the website.
Cybercriminals carry out their activities through the Tor browser in order to hide their location. Due to same reason, the payment is made only in Bitcoins (2.2 Bitcoin). Text of message depends on the user’s country and may vary. It should be noted that transferring them money, you become an accomplice in the offence. Moreover, there is no guarantee that you will obtain the promised decryption key. Instead of this, we encourage you to get rid of Crypt0L0cker ransomware safely with our help.
To prevent risk of infection by Cryptolocker ransomware follow these tips:
- Adjust your email anti-spam settings to filter out all the potentially unsafe incoming messages.
- Make sure, the attachments with the following extensions: .js, .vbs, .docm, .hta, .exe, .cmd, .scr, and .bat. place in the black list
- Rename the vssadmin.exe process to protect Shadow Volume Copies of your files from removal.
- Raise the level of protection of your Firewall. It can prevent ransomware from connecting with its server.
- Do not forget to backup your files regularly. This will facilitate process of decrypting files in case of infection.
- Install antimalware tool because it can detect ransomware in advance and remove the malware before the infection.
How Cryptolocker infects your PC?
Developers spread Cryptolocker mostly relying on email messages. In this case, victim gets message from, supposedly, legitimate company. For example, it might be bill from tax company or online store like Amazon. Of course, it piques curiosity. The virus itself is stored as an email attachment. Once launched, the process of infection will be started. Virus often use security vulnerabilities of outdated software. Therefore, keeping all your programs up-to-date reduces threat of being infected by Cryptolocker. The malware is also distributed through fake software updates, torrent (P2P) networks, and trojans.
To prevent risk of infection by Cryptolocker ransomware follow these tips:
- Adjust your email anti-spam settings to filter out all the potentially unsafe incoming messages.
- Make sure, the attachments with the following extensions: .js, .vbs, .docm, .hta, .exe, .cmd, .scr, and .bat. place in the black list
- Rename the vssadmin.exe process to protect Shadow Volume Copies of your files from removal.
- Raise the level of protection of your Firewall. It can prevent ransomware from connecting with its server.
- Do not forget to backup your files regularly. This will facilitate process of decrypting files in case of infection.
- Install antimalware tool because it can detect ransomware in advance and remove the malware before the infection.
How to remove Cryptolocker from your computer?
The best and easiest way to remove Cryptolocker from your computer is to use special anti-malware program that has this threat in its database. As stated above, you need proper and reliable anti-malware program, that’s why we recommend you to use SpyHunter.
It scans your computer and detects various threats like Cryptolocker, then completely removes it. One of the best features of this program – large threat’s database. SpyHunter’s newly advanced ransomware detection technology is able to run an instant ransomware scan and show you a message about detection. After deep scanning of your system, it will easily find and delete Cryptolocker. Use this removal tool to get rid of Cryptolocker for FREE.

How to decrypt your files encrypted by Cryptolocker?
Once you’ve removed virus, you are probably thinking of recovering files from encryption. Let’s take a look at possible ways of decrypting your data.
Recover data with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
Decrypt your files manually
You can try to use one of these methods in order to restore your encrypted data manually.
Restore data with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows saves copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore the system with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.


My system is infected with CryptoLocker. I have removed the ransomware but my all files are still encrypted and I am not able to open any files. CryptoLocker has deleted all my previous version data.
Please help me to decrypt infected files. Any software, decrypter?
At the moment, there is no tool capable of decrypting files, the only way is to use System Restore. Try to perform this step. I hope this will help you
Bonjour, je suppose qu’en 2020 c’est pareil.
Je ne comprends pas pourquoi ici ou ailleurs, ça parle de logiciel pour récupérer les données. Les fichiers sont cryptés mais ils ne sont pas “perdu” et donc les fichiers récupéré sont toujours cryptés.
Mes fichiers ont été crypté sur Android donc je n’ai pas de restauration.