What is Syrk Ransomware?
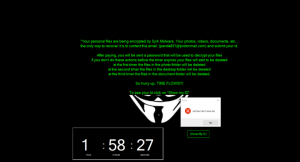
Syrk Ransomware is a type of encryption viruses. Every virus in this category has the same principles of work, that’s why we warn you: don’t try to remove Syrk Ransomware without a detailed guide, it may cause a damage. After infection with such a virus some of your files become unreadable. The reason is that such viruses encrypts your files with a special algorithm, when it’s done a file gets an appendix, in our case – .syrk. Moreover, after encryption process, in most cases you’ll receive a ransom note. Hackers seek a ransom in bitcoins, as movements of this currency cannot be traced. Concerning Syrk Ransomware, this virus encrypts your files in different folders: photos, desktop and documents. The major difference of this encryptor is that it puts timers on your desktop. When every timer expires this malware begins to delete encrypted files in one of the folders. When you try to close them it shows a message:
Error
Lol You Can't close me
It also contains a ransom note. Hacker put psychological pressure on you in order to make you pay as soon as possible:
*Your personal files are being encrypted by Syrk Malware. Your photos, videos, documents, etc...
the only way to recover it is to contact this email: (e-mail) and submit your id.
After paying, you will be sent a password that will be used to decrypt your files
if you don't do these actions before the timer expires your files will start to be deleted
at the first timer the files in the photo folder will be deleted
at the second timer the files in the desktop folder will be deleted
at the third timer the files in the document folder will be deleted.
So hurry up, TIME FLOWS!!!!
To see your Id click on *Show my ID*
It goes without saying, that you shoudn’t pay intruders! There is no guarantee that intruder will honor his promise. It’s also clear, that when intruder gets a payment, it will launch a new attack. If you want to remove Syrk Ransomware and decrypt .syrk files follow our detailed guide!
Update: It’s very important to find and remove Syrk Ransomware, as it try to be installed permanently. It will try to corrupt your USB ports, in order to spread itself by the means of different USB devices (Flashcards, mobile devices and etc), moreover it will hide to be unnoticed. We strongly recommend you to use our solution to remove Syrk Ransomware, otherwise your device and files may be corrupted forever. As far as you’ve removed the virus you may use our free guide on how to decrypt .syrk files manually or you may also use automatic decision.
Article’s Guide
- How to remove Syrk Ransomware from your computer
- How to remove Syrk Ransomware encryption from your files
- Data Recovery
- Automated decryption tools
- Windows Previous Versions
- Recover data manually
How to remove Syrk Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove Brusaf from your computer with all of its leftovers and register files.
Solution for Windows user: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like Brusaf, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to remove Syrk Ransomware encryption from your files?
Once you’ve removed the virus, you are probably thinking of recovering files from encryption. Let’s take a look at possible ways of decrypting your data.
Recover data with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
Restore data with automated decryption tools
Unfortunately, due to the novelty of Syrk ransomware, there are no available automatic decryptors for this encryptor yet. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Restore data with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore the system with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Recover data manually
There are a few types of Syrk ransomware and some of these types keep keys and IDs for decryption in the folders of your device. So there are two possible ways:
The first way
You should find dh35s3h8d69s3b1k.exe file and launch it. It’s a build-in descriptor, called Hidden-Cry. You may find it somewhere in the C:\Users\Default\AppData\ folder. If not, use Windows search engine.
The first way
As far as this encryptor keeps decryption information right on the your device, you may use these files freely. You should go to the C:\Users\Default\AppData\Local\Microsoft\ folder and look for these files: -i+.txt, -pw+.txt, and +dp-.txt. These files contain IDs and passwords, that are necessary for the decryption.


