TeslaCrypt is an add-on that can be good for internet search for those users who need to face some favourable shopping on the web. But these add-ons annoy users with different pop-ups like all bundled browser add-ons. If you do not remember if you installed the browser add-on or you repent that the software is installed, so you can read this article entirely and perform the way of removal that will be helpful to remove TeslaCrypt. If you are looking for the quick powerful software to get rid of this browser extension, so you are welcome to use the indispensable program from this page.
Automatically Manually From browsers
Main advantages of SpyHunter:
- Eliminates all component parts generated by TeslaCrypt.
- Is able to fix browser problems and protect browser settings.
- Has System and Network Guards, so you can forget about malware.
What is TeslaCrypt?
TeslaCrypt is not harmful software since it cannot affect other computers, but it can be installed with different freeware. This fact makes a feeling that TeslaCrypt is a PC infection.
But, actually, it is just an nerve-racking add-on that worries you the means of advertising report in the form of popping-up windows. Almost everyone has unwanted browser extensions like TeslaCrypt and wants to get rid of it.
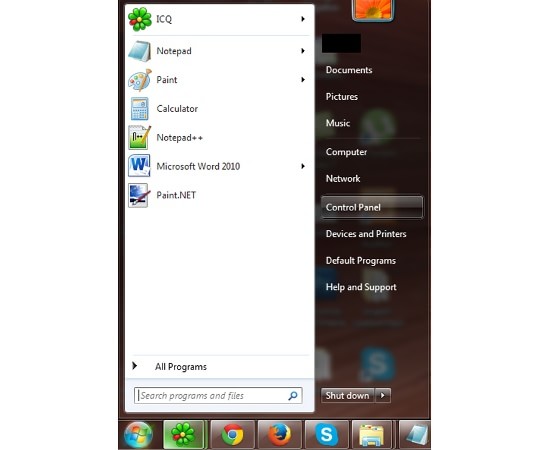
1. Install TeslaCrypt Removal Tool:

Step 1. Click Start button
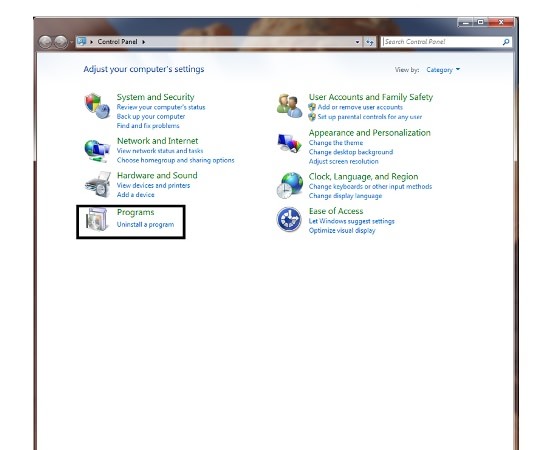
Step 2. Choose Control Panel
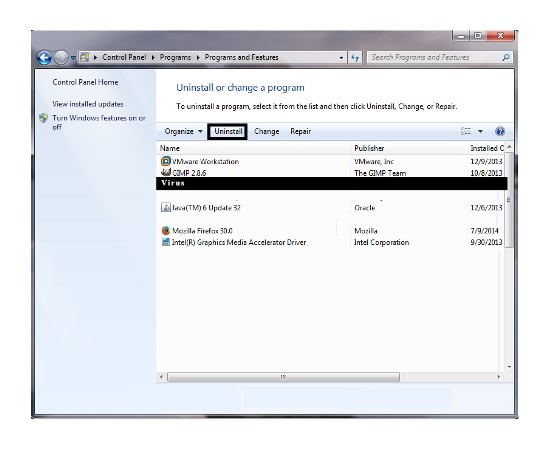
Step 3. Highlight the annoying software and press Uninstall
![]()
Files:
- No information
![]()
Folders:
- No information
![]()
Registry Entries:
- No information

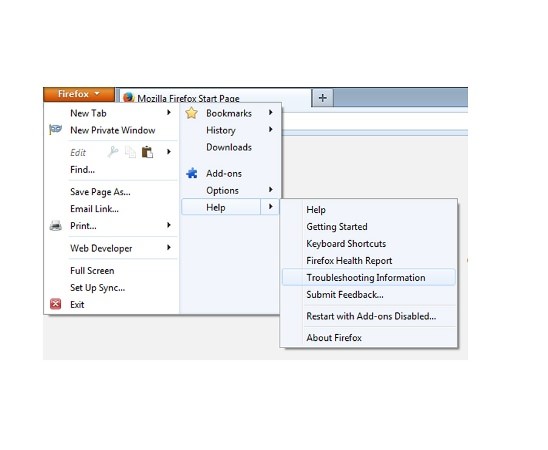
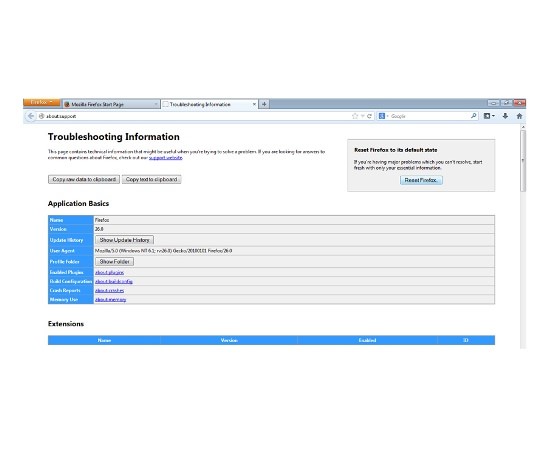
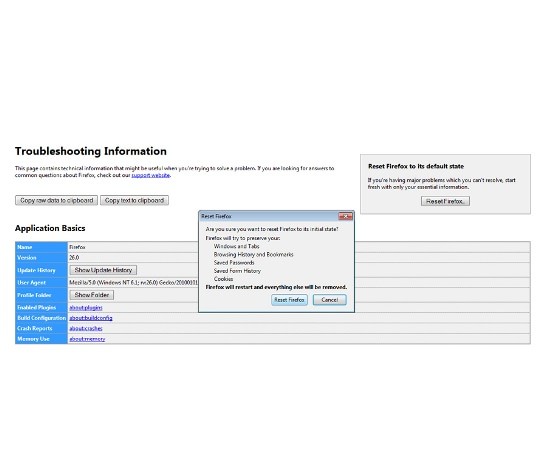
Uninstall TeslaCrypt from Firefox:
- Help=>Troubleshooting Information
- Reset Firefox
- Finish

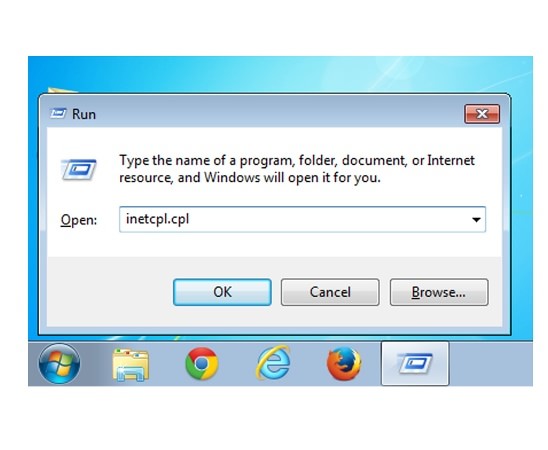
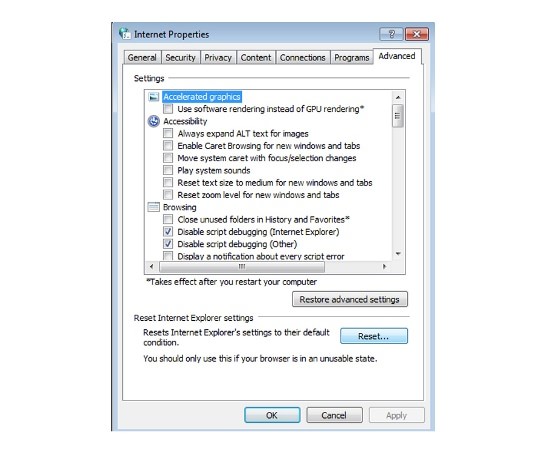
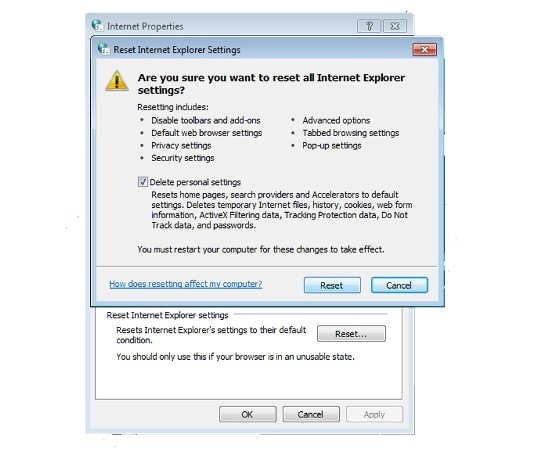
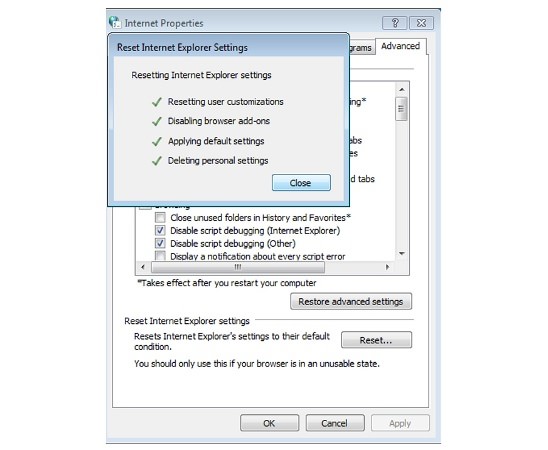
Delete TeslaCrypt from IE:
- Run inetcpl.cpl
- Advanced=>Reset
- Delete Personal Settings=>Reset=>Close

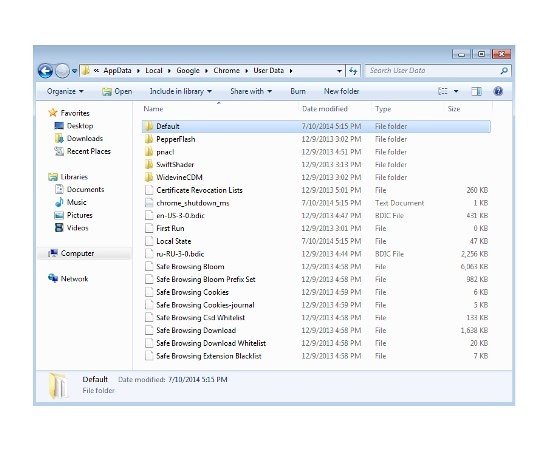
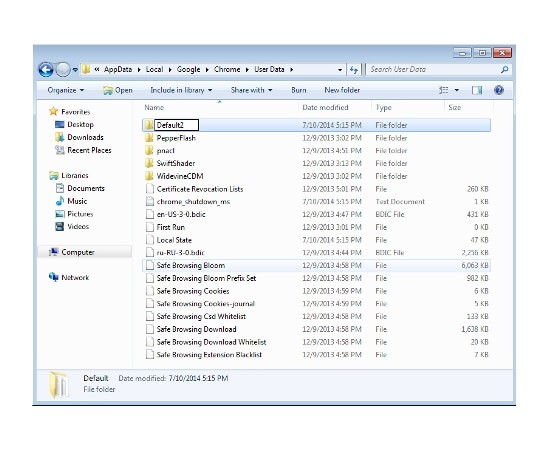
Remove TeslaCrypt from Google Chrome:
- C:\Users\”your username”\AppData\Local\Google\Chrome\Application\User Data
- Rename Default folder to Default2
- Open Google Chrome
- Do not open Opera
- Remove Profile and Cache folders in:
- C:\Users\User_Name\AppData\Roaming\Opera Software\Opera Stable
- C:\Users\User_Name\AppData\Local\Opera Software\Opera Stable
- Open Opera
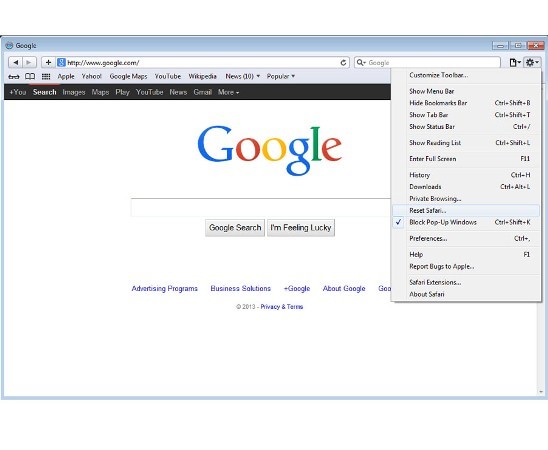
- Open your browser
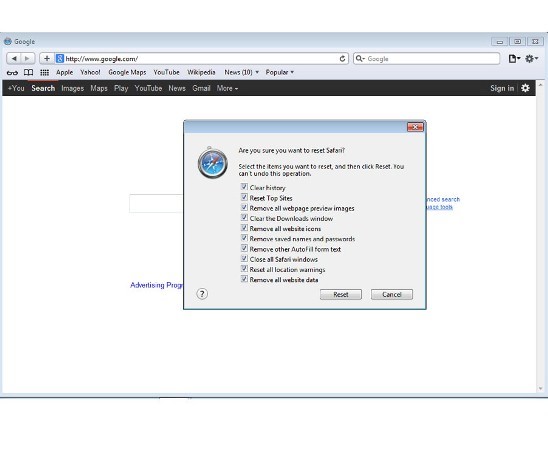
- Settings->Reset Safari
- Reset
Every user should realize that all the programs for browsers including TeslaCrypt, no matter if they are useful, are the areas of weakness for every browser where they are installed. The software companies that created browsers release update patches regularly, due to which the browser safety is protected. The occurrence of any extension can make the effort to defend the security of the browser impossible. And, as a result, some online offenders can use your computer or collect your sensible info. If you are not able to imagine your browser without browser extensions, then I advise to install browser programs from dependable software vendors only, may be it will assist you to protect the computer. But you should understand that it is better not to download any browser add-ons at all.
But if you still want to install any browser extension in that case you should be ready that the extension will get compliance to collect your private information that you enter on various websites and can pass it to the third parties. You should realize that to install a browser add-on is the same case that toinstall a program. Will you install software if its software company is unreliable? I advise you not to. So, you also should be careful downloading the browser add-on that you want to install.
TeslaCrypt is a browser extension that brings trouble. Is there any guarantee that the deals are 100% true? Certainly, no. So, you should not believe the ads and its promises. Also you should not visit the landing pages of the displayed pop-ups for they can be viral and so, in its train, your PC can be infected with a true viral program on your PC.
| Damage Level |
Medium
PUP |
| Data Theft | 62,4% |
| System Failure | 0,01% |
| Manual Removal | 20 |
| Removal From Browsers | 38,3% |
| Removal with Free Antivirus | 45,6% |
| Removal with SpyHunter | 97,2% |
| Infected computers (USA) | 0,001% |
| Infected computers (Europe) | 0,0021% |
| Browser Infection Probability | 54,2% |
TeslaCrypt like other adware software has a few common symptoms that will help you to detect if your PC is infected with it or not. Here is the list of them:
- Many pop-ups shown by TeslaCrypt
- Very sluggish system
- Antivirus software detects some computer infections
- Changes in your browser (toolbars, homepage, search engine)
- Search results are hijacked
- TeslaCrypt adds its files, folders and registry entries
Manual and Automatic Removal Methods?
Manual removal method that you can execute to uninstall TeslaCrypt from browsers are safe and not so difficult as you might think. Possibly, only automatic method is easier. This removal way is very efficacious since the browser vendors care about your right to add or remove any browser add-ons. This method will give you a chance to delete all the unwanted browser extensions and you will not be shown its advertisements any more. But sometimes, using this technique users notice that the program returns to the browser and they have to find any other techniques to delete it.
Also there is one more manual removal instruction using which you should delete files and registry keys and values. The described way of removal is secure in case if you will perform it carefully or let the expert follow it. To make this process safer you should create the backup of the registry. You should keep in mind that only the itemized elements of the extension should be enumerated and no other ones otherwise your PC will not load. If you do not understand what registry value is and where it should be found, then it is better to use automatic way of removal not to break your computer.
Automatic technique is the method when a user runs any removal utility to solve the problem. This method is the most secure and sure. It is also not a difficult one. You can just download the antivirus program that has TeslaCrypt in its signature base. This technique is more helpful because you will have the antispyware and antimalware scanner that will guard the system against the future incoming threats.
Concerning the sums of money that users may spend on the removal of the virus I should say that some methods are absolutely free, for example manual removal from browsers, manual professional removal (in the case if you will do it by yourselves), free antivirus software and the removal from Control Panel. But not all of them are powerful. The information about the effectiveness of these methods I illustrate in the table that is called ‘Removal methods statistics’ below. Speaking about the paid techniques of virus removal, I should mention the Computer Repair Shop Service and paid Antivirus software.
These methods are the most efficient. In spite of the great inequality in the price (Repair Shop service depends on the complexity of the issue and may cost up to $300, but paid antivirus costs up to $60) these removal techniques are almost equal in the effectiveness and in the results. I should also say that paid antiviruses always has support service (often for free) that will remove the virus like in an expensive computer repair shop.
Removal methods statistics
| Removal method | Price | Effectiveness | Safety | Needed Time |
| Computer Repair Shop | $175-$210 | +++ | +++ | up to 4 days |
| Paid Antivirus | $35-70 | +++ | +++ | up to 1 hour |
| Free Antivirus |
$0 | +/- | +/- | up to 3 hours |
| From Control Panel | $0 | +/- | ++ | up to 1 hour |
| Manual Removal (Professional) | $0 | + | – | up to 4 Hours |
| Removal from browsers | $0 | +/- | +/- | up to 1 hour |
There is a great deal of useful tools and other antimalware software that can be downloaded to eliminate TeslaCrypt and you can use any of them, but I suggest you SpyHunter. This program is the best TeslaCrypt Removal Tool to my mind. Uninstalling the adware you also will have the opportunity to defend your system.
Enigma Software created SpyHunter to be a efective antispyware and antimalware utility that can guard the computer against all modern viral objects, including rootkits, trojans and keyloggers. Thanks to the regularly renewed base of signatures SpyHunter can remove all the actual viruses that are created by malware writers every day.
Then recent version of SpyHunter not only vary its interface to more handy and pretty, yet the utility does not conflict with other antivirus tools that you can download. Also this utility works faster and protects better.
SpyHunter gives real-time protection, has Integrated SpyHunter Compact OS that let to delete the most stubborn computer threats and the dependable live technical support. SpyHunter is compatible with Windows 98/ME/NT/2000/XP/2003/Vista/Seven/8, it needs 256 MB of RAM, 75 MB of available hard disk space.
How to use SpyHunter
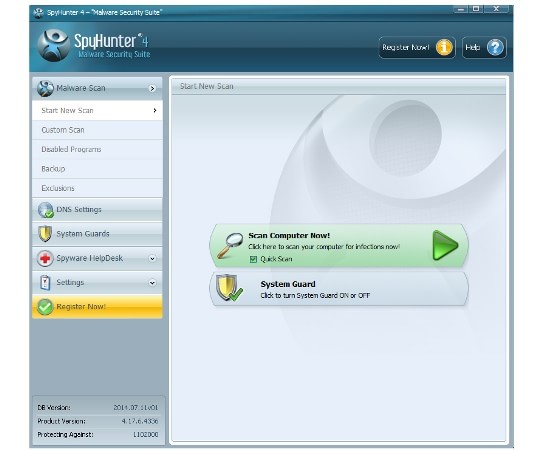
You are welcome to left-click the link on this article to download SpyHunter. Open that installer and follow the necessary steps. Choose the language that is understandable for you. Fortunately SpyHunter has a lot of them, being useful and easy-to-use. But not only this makes SpyHunter very famous all outdoors, but also its great capability to guard users’ PC.
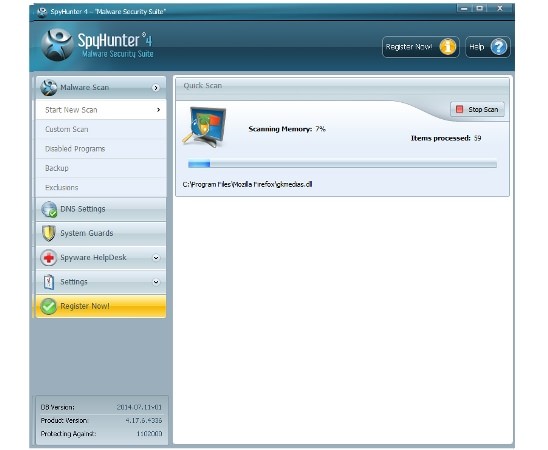
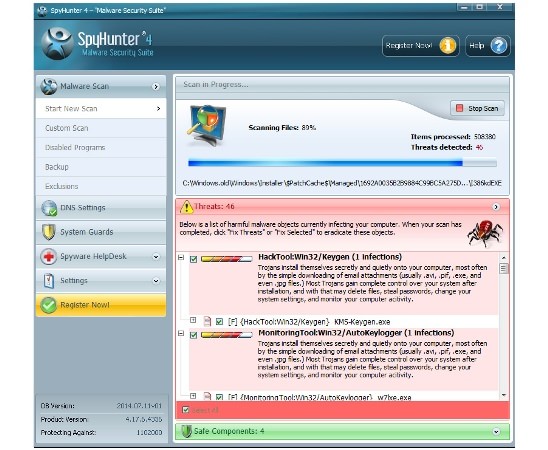
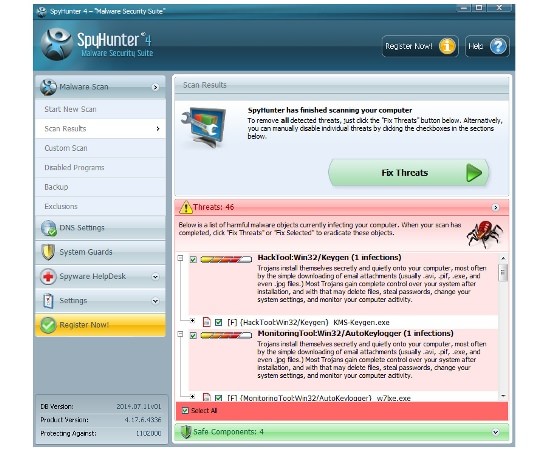
After installation, you should update it, if the software does not do it by itself when you run it for the first time. When the program is updated you need to run the Scan process. Usually it is enough to run fast scan in order to find and remove all the viruses and undesired items in the system.
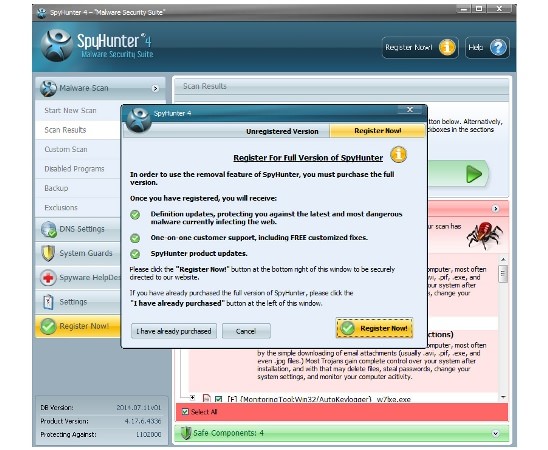
After the scan it is better to look into the results and deactivate the ticks near the needed utilities that Shyhunter referred to viral or undesired tools. Then you can click Fix Threats. If you have already bought the license key, then the viruses will be eliminated. If not, then you you can do it now.
This guide describes some methods to remove TeslaCrypt, I hope, they were effective for you and the unwanted program for browser is uninstalled. Still your system is at stake every day and so it should be protected. I advise you to download an antivirus program that will save your system every day and will let you to your system at least one time a week The downloaded antispyware program should have a broad virus database and everyday releases of updates. The most effective antivirus tools has real-time protection. It is the protection that is able to reveal computer threats in the system when it is just trying to infect your system.
If you do not know what antivirus protection to download, then I suggest you to download SpyHunter. The utility will absolutely delete all the computer threats and will provide you with a real-time block to guard the computer from the incoming viruses. It is very easy to scan your system with SpyHunter and it is so useful that can reveal and remove rootkits and trojans and other malware that are recondite deep in the system. If you have any useful utility for you work, but SpyHunter reveals it as a computer threat and you are absolutely certain that this program cannot b a virus, so you can add it to Exclusions list and SpyHunter will not detect it as a malicious software. If you want to scan just one folder, then can choose Custom Malware Fixes option. You can also take advantage of Process Guard or Registry Guard of this antivirus program for your convenience.
I also want to advice you some useful things that will protect your computer from TeslaCrypt and other computer threats in the future:
- Do not install any free programs from unknown vendors. If you do not want to pay for programs, then you should be very careful during the installation of the application. You should not miss the checkbox (usually small letters) that is responsible for the installation of any other free programs. You should uncheck this checkbox.
- Do not visit any dangerous websites (porn, for adults, websites of unknown free software), they usually contain some worms or other variants of malicious programs.
- Do not use torrents or other sharing web services, because you can download exe file instead of the needed file.
- Do not double-click email attachment from unknown persons. It can be one of the computer dangers.
- Install any antivirus software and scan your system at least once a week.
Video Instructions to remove TeslaCrypt
About Author: Material provided by: Alesya Orlova


 Download SpyHunter right here
Download SpyHunter right here