Article’s Guide
- What does Файл зашифрован. Пиши noallpossible@cock.li .happy new year stand for?
- WannaCash ransomware encryption process.
- How to remove WannaCash Ransomware from your computer
- How to decrypt Файл зашифрован. Пиши noallpossible@cock.li .happy new year files
- Data Recovery
- Automated decryption tools
- Other software
What does “Файл зашифрован. Пиши noallpossible@cock.li .happy new year” mean?
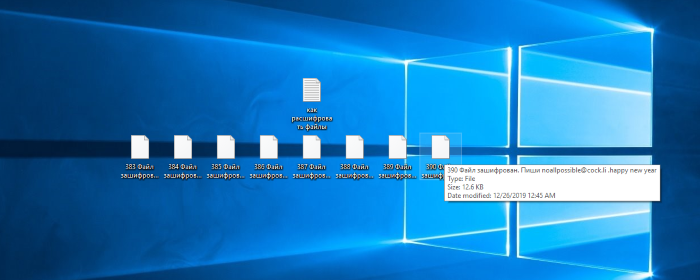
If you see, that the names of your files have been changed to “Файл зашифрован. Пиши noallpossible@cock.li .happy new year”, your files are really encrypted. Such renaming of files is a characteristic feature of WannaCash ransomware, to be more exact of its newest modification. The use of Russian language in the extension and the ransom note is suggestive of the fact that this virus is aimed at the Russian speaking countries, however, anyone potentially can face it. This virus can be easily spread by the means of email attachments, fake installators, downloaded by the other virus, or even installed by the means of RAT. Nowadays ScreenConnect service is popular among hackers. This soft allows them to get nearly full control over computers. Moreover, hackers widely use botnet viruses, that also give them control over devices. It’s very difficult to notice the infection with such a virus and a great amount of antiviruses can’t find them. Moreover, they can’t notice WannaCash ransomware, so it’s necessary to have a strong antivirus protection nowadays. If your device is already infected with this virus, don’t try to remove WannaCash ransomware or to decrypt “Файл зашифрован. Пиши noallpossible@cock.li .happy new year” files without a special tool. Such infection are always complex and it requires a full scan of your system.
WannaCash ransomware encryption process.
WannaCash ransomware has common encryption mechanics. At first the virus makes necessary modifications in an operating system. It’s necessary to make a protection of a computer believe, that the harmful processes are legitimate. Then it proceeds scanning of the hard drive and begins to modify files. A very interesting feature of WannaCash ransomware is the way it modifies files.It renames them fully. It adds a number to a file and the new extension – “Файл зашифрован. Пиши noallpossible@cock.li .happy new year”. Then the virus drops the ransom note, called “Как расшифровать файлы.txt”. Unfortunately, nowadays the only method to surely decrypt 100% of the encrypted data is to get the key from the criminals. However, we strongly recommend you not to do it. As the rule, hackers stop all contacts with the victims, once they’ve been paid. Moreover, there is a great risk, that your device is infected with several viruses, that will continue their work. For this case, we’ve prepared the detailed guide on how to remove WannaCash ransomware, possible threats and to decrypt your files.
██████████████████████████████████████████████ ╔=====================================================================================================================================================================╗
Как расшифровать файлы.txt
█─███─█────█─██─█─██─█────█────█────█───█─██─█
█─███─█─██─█──█─█──█─█─██─█─██─█─██─█─███─██─█
█─█─█─█────█─█──█─█──█────█─████────█───█────█
█─────█─██─█─██─█─██─█─██─█─██─█─██─███─█─██─█
██─█─██─██─█─██─█─██─█─██─█────█─██─█───█─██─█
██████████████████████████████████████████████
║ ║
║ Все значимые файлы на ВАШЕМ компьютере были упакованы в закодированные архивы с уникальными 100''значыми паролями, при использованием AES-256-битного шифрования. ║
║ ║
║ Пораженные расширения и типы: ║
║ .doc .docx .xls .xlsx .xlst .ppt .pptx .accdb .rtf .pub .epub .pps .ppsm .pot .pages .odf .odt .ods .pdf .djvu .html .rtf .1Cv8ddb.1cl .1CD .cf .dt .efd .jpg .png ║
║ .mp4 .mov .avi .mpeg .flv .gif .bmp .3gp .zip .rar'+' .7z .gzip .gz .tib .bak .iso .dat .cpp .h .pas .dpr .dproj .py .JS .css .php .asm .jar .apk .xml .psd .psb ║
║ .AEPX .PRPROJ .SWF .veg .txt .bd .default "Cookies" "History" "Login Data" "Favicons" "Web Data" "default" ║
║ ║
║ ……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… ║
║ ║
║ Я гарантирую, что ВЫ сможете безопасно и легко восстановить все свои файлы. ║
║ Чтобы подтвердить мои честные намерения, отправьте мне на почту 2 разных файла, и ВЫ получите их расшифровку. Они НЕ должны быть документами (офис и тп). ║
║ ║
║ ……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… ║
║ ║
║ почта: noallpossible@cock.li ║
║ резеврная почта: supermax@cock.lu ║
║ Если не отвечаю в течении суток, пишите на резервную почту. ║
║ ║
║ ……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… ║
║ ║
║ У ВАС есть ровно 7 дней на связь со мной. 01.01.2020 числа в расшифровке ВАМ будет отказано. ║
║ ║
║ ……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… ║
║ ║
║ Внимание ! ║
║ * Не переименовывайте зашифрованные файлы. ║
║ * Не пытайтесь расшифровать ваши данные с помощью сторонних программ, это может привести к повреждению или другим неприятным последствиям. ║
║ ║
║ Крайне не рекомендую обращаться за помощью на форумы антивирусных компаний. Только лишь потеряете время на ожидание отрицательного ответа. ║
║ ║
╚=====================================================================================================================================================================╝
Как расшифровать файлы.txt translation
Infected formats and types:
.doc .docx .xls .xlsx .xlst .ppt .pptx .accdb .rtf .pub .epub .pps .ppsm .pot .pages .odf .odt .ods .pdf .djvu .html .rtf .1Cv8ddb.1cl .1CD .cf .dt .efd .jpg .png
.mp4 .mov .avi .mpeg .flv .gif .bmp .3gp .zip .rar'+' .7z .gzip .gz .tib .bak .iso .dat .cpp .h .pas .dpr .dproj .py .JS .css .php .asm .jar .apk .xml .psd .psb
.AEPX .PRPROJ .SWF .veg .txt .bd .default "Cookies" "History" "Login Data" "Favicons" "Web Data" "default"
I guarantee, that you can easily restore your files
In order to prove my honesty, you can send me two files, and they will be decrypted. They are to be NOT documents (office and etc.)
Email: noallpossible@cock.li
Reserve email: supermax@cock.lu
If I don't respond in a day, write to the reserve email.
You have only 7 days, *data* you will be refused in decryption!
Attention!
*Don't rename encrypted files.
*Don't try to decrypt your files by the means of 3rd party software, as it can damage your files or something else.
I strongly recommend you to avoid forums of antivirus companies. You will lose your time.
How to remove WannaCash Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove WannaCash from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like WannaCash, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt Файл зашифрован. Пиши noallpossible@cock.li .happy new year files?
Once you’ve removed the virus, you are probably thinking how to decrypt Файл зашифрован. Пиши noallpossible@cock.li .happy new year files or at least restore them. Let’s take a look at possible ways of decrypting your data.
Restore Файл зашифрован. Пиши noallpossible@cock.li .happy new year with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Decrypt Файл зашифрован. Пиши noallpossible@cock.li .happy new year files with other software
Unfortunately, due to the novelty of WannaCash ransomware, there are no decryptors that can surely decrypt encrypted files. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Decrypt Файл зашифрован. Пиши noallpossible@cock.li .happy new year files with Emsisoft decryptor
This software includes information about more than 100 viruses of STOP(DJVU) family and others. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.
Restore Файл зашифрован. Пиши noallpossible@cock.li .happy new year files with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore Файл зашифрован. Пиши noallpossible@cock.li .happy new year files with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Was this tutorial helpful?[Total: 0 Average: 0]
This software includes information about more than 100 viruses of STOP(DJVU) family and others. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore Файл зашифрован. Пиши noallpossible@cock.li .happy new year files with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Was this tutorial helpful?[Total: 0 Average: 0]
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.