What is Serpent?
Serpent is a new file-encrypting virus primarily focused on Danish users. This is evidenced by the fact that the malicious email used to infect computer contains message in Danish (“Sidste påmindelse for udestående faktura 1603750” which translates to “Last reminder for outstanding invoice 1603750”). After infiltration, Serpent ransomware corrupts your personal and sensitive files, like images, music, videos, text files and so on. At the same time, this ransomware adds .serpent or .dng file extension to the name of all the target files. For example, “document.doc” is renamed to “document.doc.serpent”.
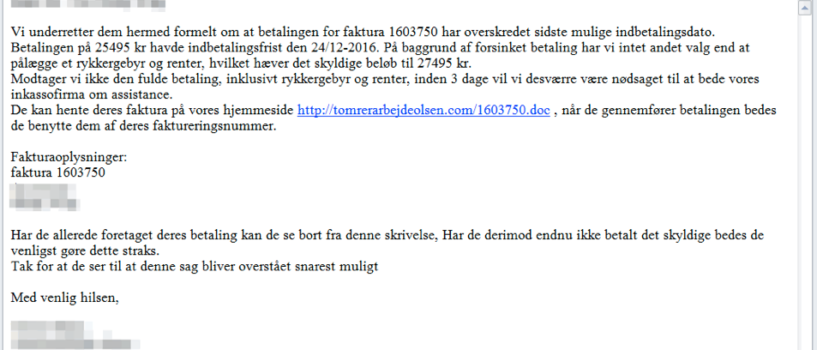
Once encrypted, it creates two files in each folder with encrypted files: “HOW_TO_DECRYPT_YOUR_FILES_Dn6.txt” and “HOW_TO_DECRYPT_YOUR_FILES_Dn6.html”. These files provide us instruction on how to restore files. Like other similar types of viruses, Serpent uses typical ransomware scheme to force you to pay them. In these cases, cyber criminals usually state that there are no ways to decrypt your data but to pay ransom. Amazingly, Serpent ransomware claims that it uses AES-256 and RSA-2048 complex cryptographic algorithms. In this case, decryption is not available without special key which cyber criminals keep on a remote server. However, it’s just a trick to scare users, actually, this virus does not encrypt files, but rename your files by adding .serpent or .dng file extension. That’s why you shouldn’t trust them and transfer money. Especially as you can restore files yourself. From this article, you will learn how to remove Serpent ransomware and decrypt .serpent or .dng files for FREE.
This is what the ransom note contains:
==== NEED HELP WITH TRANSLATE? USE https://translate.google.com ====
================ PLEASE READ THIS MESSAGE CAREFULLY ================Your documents, photos, videos, databases and other important files have been encrypted!
The files have been encrypted using AES256 and RSA2048 encryption (unbreakable)
To decrypt your files you need to buy the special software ‘Serpent Decrypter’.
You can buy this software on one of the websites below.
hxxp://vdpbkmwbnp.pw/
hxxp://hnxrvobhgm.pw/
If the websites above do not work you can use a special website on the TOR network. Follow the steps below
1. Download the TOR browser https://www.torproject.org/projects/torbrowser.html.en#downloads
2. Inside the TOR browser brower navigate to : 3o4kqe6khkfgx25g.onion/
3. Follow the instructions to buy ‘Serpent Decrypter’================ PLEASE READ THIS MESSAGE CAREFULLY ================
How Serpent infects your PC?
Like any other ransomware-type viruses, Serpent ransomware is distributed primarily through the fraudulent email messages. For example, it might be bill from tax company or online store like Amazon. The virus itself is hided within an attachment. Therefore, be very wary when opening files downloaded from suspicious emails or untrusted sources. Do not rush in these moments since you can compromise your system. The malware is also distributed through fake software updates, torrent (P2P) networks, and trojans as well.
To prevent suсh kinds of the threats as Serpent ransomware in the future follow these tips:
- Adjust your email anti-spam settings to filter out all potentially unsafe incoming messages.
- Make sure, the attachments with the following extensions: .js, .vbs, .docm, .hta, .exe, .cmd, .scr, and .bat. are in the black list
- Rename the vssadmin.exe process to protect Shadow Volume Copies of your files from removal.
- Raise the level of Firewall protection. It can prevent ransomware from connecting with its server.
- Do not forget to backup your files regularly. This will facilitate process of decrypting files in case of infection.
- Install antimalware tool because in most cases, it can detect ransomware in advance and remove the malware before the infection.
How to remove Serpent from your computer?
The best and easiest way to remove Serpent from your computer is to use special anti-malware program that has this threat in its database. As stated above, you need proper and reliable anti-malware program, that’s why we recommend you to use SpyHunter.
It scans your computer and detects various threats like Serpent, then completely removes it. One of the best features of this program – large threat’s database. SpyHunter’s newly advanced ransomware detection technology is able to run an instant ransomware scan and show you a message about detection. After deep scanning of your system, it will easily find and delete Serpent. Use this removal tool to get rid of Serpent for FREE.
How to decrypt .serpent or .dng files encrypted by Serpent?
Once you’ve removed virus, you are probably thinking of recovering files from encryption. Let’s take a look at possible ways of decrypting your data.
Recover data with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
Decrypt .serpent or .dng files manually
You can try to use one of these methods in order to restore your encrypted data manually.
Restore data with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows saves copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore the system with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.


