ReadTheInstructions ransomware encryption process.
It goes without saying, computers and the internet are the parts of our everyday life. Nearly every computer and gadget have the access to the internet and it’s very convenient. However, the internet is full of threats, that can possibly destroy your life. The one of them is ReadTheInstructions ransomware. This ransomware belongs to the Medusalocker file-encryption ransomware family. This family has a lot in common with such widespread viruses, as STOP(DJVU) ransomware family:MBED, PEET, GROD, MOSK, TOEC, NAKW, Derp, COOT, Nols, Werd, Ndarod, Leto, Bora and RECO; and DHARMA file-encryption ransomware family the members of which are: KHARMA, newer version of MONEY, Money, Oo7 and CASH. It’s very easy to become infected with these viruses, as they are usually hidden in harmless files. The hackers inject the code of the virus into a file and it executes, once a user decides to open this file. Such files can be easily found, as they spread by the means of file sharing services, torrent trackers and other websites. Moreover, hackers can send to you directly: it’s a common practice, when hackers write an email as if they are representatives of a well known company or apply for a job. In the case of such messages, the infected file is attached to it. If your device has been accidentally infected with this virus, don’t try to remove ReadTheInstructions ransomware encryption manually! Renaming of file can potentially damage it!
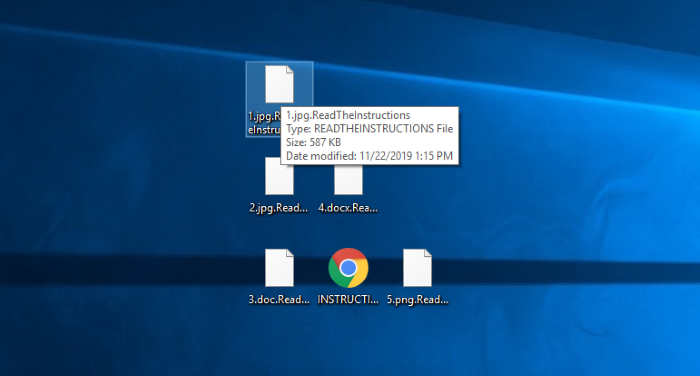
When ReadTheInstructions ransomware sneaks into the system, it begins the encryption process, that can be characterized as the two-step one. The first step is the scanning of the hard drive and searching for the files appropriate for encryption. ReadTheInstructions ransomware encrypts only media files and documents, as the encryption of all files is a very time-consuming operation. When the files are found, the virus begins to modify them and as the result the files have new extension .ReadTheInstructions and are unreadable. Then the virus creates a ransom note in the form of HTML document, that is called INSTRUCTIONS.html. this message aims at promotion of the hackers’ decryption services. In this message hackers try to assure the user, that only they can decrypt these files. However, there is no any firm guarantee , that they will decrypt your files once they receive your payment. It’s a great risk to trust criminals. Moreover, the situation can become even worse, as they can easily send a malware instead of the decryption tool. If you really need to remove ReadTheInstructions ransomware and decrypt .ReadTheInstructions files, you’d better use our guide!
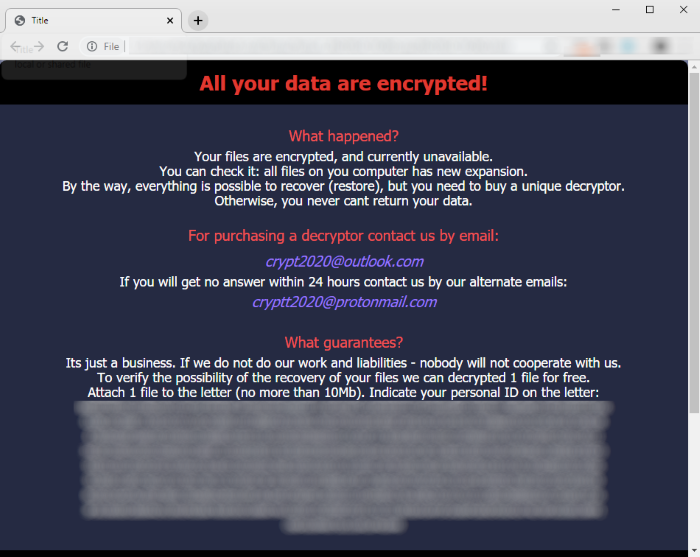
All your data are encrypted!
Your files are encrypted, and currently unavailable.
You can check it: all files on you computer has new expansion.
By the way, everything is possible to recover (restore), but you need to buy a unique decryptor.
Otherwise, you never cant return your data.
For purchasing a decryptor contact us by email:
crypt2020@outlook.com
If you will get no answer within 24 hours contact us by our alternate emails:
cryptt2020@protonmail.com
What guarantees?
Its just a business. If we do not do our work and liabilities - nobody will not cooperate with us.
To verify the possibility of the recovery of your files we can decrypted 1 file for free.
Attach 1 file to the letter (no more than 10Mb). Indicate your personal ID on the letter:
*ID*
Attention!
- Attempts of change files by yourself will result in a loose of data.
- Our e-mail can be blocked over time. Write now, loss of contact with us will result in a loose of data.
- Use any third party software for restoring your data or antivirus solutions will result in a loose of data.
- Decryptors of other users are unique and will not fit your files and use of those will result in a loose of data.
- If you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause just we have the private key.
Article’s Guide
- How to remove ReadTheInstructions Ransomware from your computer
- How to remove ReadTheInstructions Ransomware encryption from your files
- Data Recovery
- Automated decryption tools
- Windows Previous Versions
How to remove ReadTheInstructions Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove ReadTheInstructions from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like ReadTheInstructions, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt .ReadTheInstructions files?
Once you’ve removed the virus, you are probably thinking how to decrypt .ReadTheInstructions files. Let’s take a look at possible ways of decrypting your data.
Recover data with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Restore data with automated decryption tools
Unfortunately, due to the novelty of ReadTheInstructions ransomware, there are no available automatic decryptors for this encryptor yet. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Remove ReadTheInstructions encryption with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Remove ReadTheInstructions encryption with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Was this tutorial helpful?[Total: 0 Average: 0]
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.


I have installed the program and it did not work. I contacted the software company, they indicated this program is not for this ransomware. They don’t know who said it will work ?