Article’s Guide
- What does .pashka stand for?
- Quimera ransomware encryption process.
- How to remove Quimera Ransomware from your computer
- How to decrypt .pashka files
- Data Recovery
- Automated decryption tools
- Other software
What does .pashka stand for?
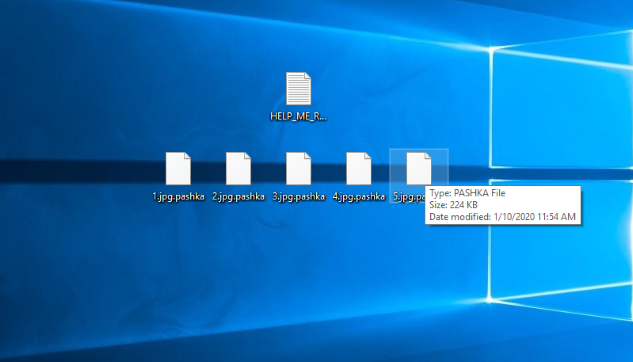
Recently the newest threat has attacked a great number of personal computers. This threat is Quimera ransomware. The characteristic feature of this virus is .pashka extension, that is added to the end of the files’ names. This virus doesn’t belong to any already known family of viruses, however, it has the same features with well known ones, such as STOP(DJVU), Medusa Locker and DHARMA. As far as it’s known, this virus spreads by the means of fake installators. It’s interesting, that the creators of Quimera virus hack YouTube channels in order to promote the file, that contains this virus. However, nowadays it’s not the only way to distribute it. Hackers can also infect your computer with a remote access software, that gives them an opportunity to install Quimera virus remotely without any suspect. Moreover, they can easily spread it by the means of fake emails. Hackers often write messages, as if they are representatives of a well-known company, such as DHL, by the means of which they try to force a victim to open an infected file. On the basis of the previous statements, we strongly recommend you to have a strong antivirus protection, that can prevent a potential attack. If you are unlucky and your device is already infected with this virus, don’t try to rename .pashka files! Such modification of a file can easily damage it.
Quimera ransomware encryption process.
The Quimera ransomware encryption process can be described as a very complex one. At first the Quimera makes some changes in the Registry in order to launch itself with the next startup of an infected computer. Then it injects into a memory of another process in order to stay undetected. At the same moment it checks if it’s started in a virtual machine or not. In the end it begins the scanning process in order to find files, that can be modified. In the most cases such files are all formats of media files and documents, however, Quimera can also easily modify archives and databases. When the files are found, Quimera immediately begins to modify them and makes them unreadable. The easiest way to identify this virus is “.pashka” extension, that is added to the files’ names and ransom note, that is called “HELP_ME_RECOVER_MY_FILES.txt”. By the means of this note hackers try to force a victim to pay for the decryption services, that they offer. Unfortunately, only they can surely decrypt your files, however, there is a great number of cases, when ransoms refuse to fulfil their promises. As far as they are paid, criminals just stop all contacts with the victims. Moreover, they can even make the situation much worse. They can send you a malicious software instead of the a decryptor and easily destroy all your data. That’s why we strongly recommend you to avoid any contact with them and check your system with a powerful antivirus. If you really need to decrypt your data and get rid of this virus, read our detailed guide on how to remove Quimera ransomware and decrypt .pashka files!
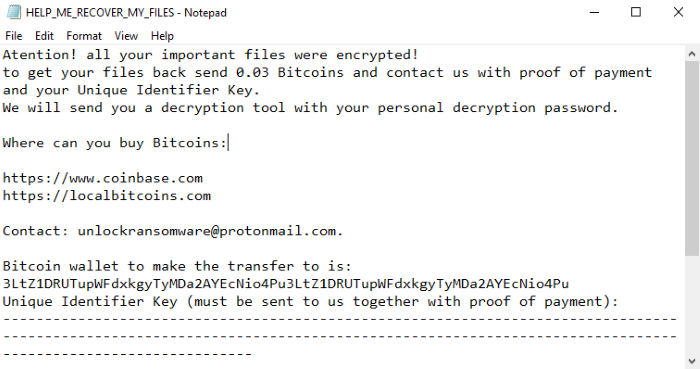
HELP_ME_RECOVER_MY_FILES.txt
to get your files back send 0.03 Bitcoins and contact us with proof of payment and your Unique Identifier Key.
We will send you a decryption tool with your personal decryption password.
Where can you buy Bitcoins:
https://www.coinbase.com
https://localbitcoins.com
Contact: unlockransomware@protonmail.com.
Bitcoin wallet to make the transfer to is:
3LtZ1DRUTupWFdxkgyTyMDa2AYEcNio4Pu3LtZ1DRUTupWFdxkgyTyMDa2AYEcNio4Pu
Unique Identifier Key (must be sent to us together with proof of payment):
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
*Key*
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
How to remove Quimera Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove Quimera from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like Quimera, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt .pashka files?
Once you’ve removed the virus, you are probably thinking how to decrypt .pashka files or at least restore them. Let’s take a look at possible ways of decrypting your data.
Restore .pashka files with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Decrypt .pashka files with other software
Unfortunately, due to the novelty of Quimera ransomware, there are no decryptors that can surely decrypt encrypted files. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Decrypt .pashka files with Emsisoft decryptor
This software includes information about more than 100 viruses of STOP(DJVU) family and others. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.
Restore .pashka files with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore .pashka files with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Was this tutorial helpful?[Total: 0 Average: 0]
This software includes information about more than 100 viruses of STOP(DJVU) family and others. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore .pashka files with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Was this tutorial helpful?[Total: 0 Average: 0]
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.