DECP ransomware encryption process
DECP malware is classified as the ransomware, that belongs to the Matrix Ransomware family. The functions of this malicious software are to change file structures in order to make them unreadable. Hackers use a number of tricks to infect your device, such as spam emails, brute forcing, fake software and etc. We warn you, that it’s dangerous to open suspicious links and email attachments, as the virus infects systems in almost no time at all. The injection can hardly be noticed as well as the encryption process. The result of it always the same – the user can’t open some of the files, as their original extensions have been changed to .[deccrypasia@yahoo.com].*random*.DECP ones. Don’t remove DECP ransomware extensions by the file renaming or other manual method, as it may lead to unpreventable damage of your data. Hackers mostly create ransom notes that provide you with the information about the price of the decryption and contacts. In the case of DECP encryptor, it’s called #DECP_README#.rtf and it contains the following information:
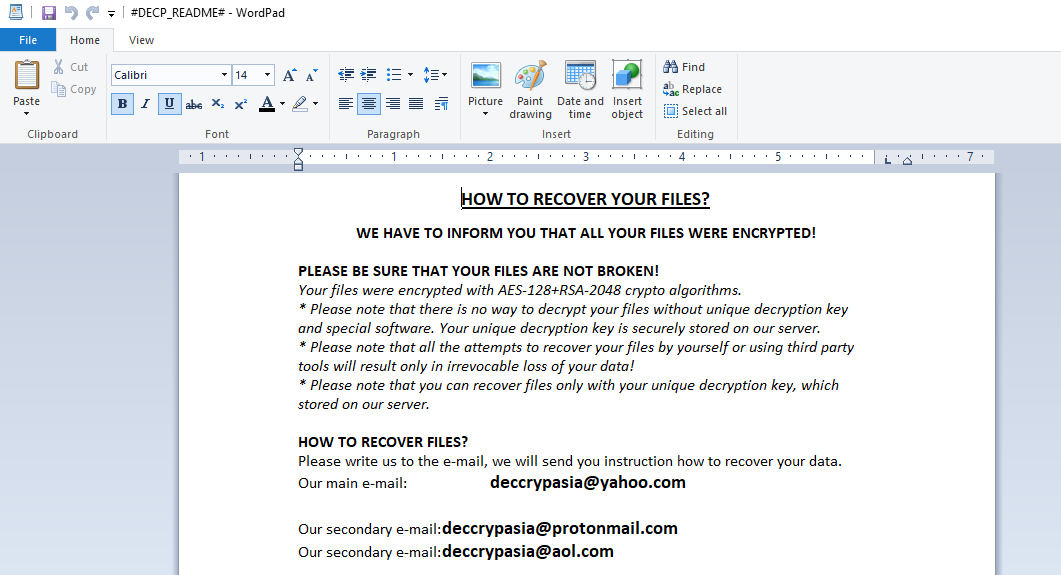
HOW TO RECOVER YOUR FILES?
WE HAVE TO INFORM YOU THAT ALL YOUR FILES WERE ENCRYPTED!
PLEASE BE SURE THAT YOUR FILES ARE NOT BROKEN!
Your files were encrypted with AES-128+RSA-2048 crypto algorithms.
* Please note that there is no way to decrypt your files without unique decryption key and special software. Your unique decryption key is securely stored on our server.
* Please note that all the attempts to recover your files by yourself or using third party tools will result only in irrevocable loss of your data!
* Please note that you can recover files only with your unique decryption key, which stored on our server.
HOW TO RECOVER FILES?
Please write us to the e-mail, we will send you instruction how to recover your data.
Our main e-mail: deccrypasia@yahoo.com
Our secondary e-mail: deccrypasia@protonmail.com
Our secondary e-mail: deccrypasia@aol.com
Please write to our main e-mail. If you will not receive answer in 24 hours, please write to our secondary e-mails! Please always check SPAM folder!
* Write on English or use professional translator
In subject line write your personal ID: *ID number*
For your assurance you can attach up to 3 small encrypted files to your message. We will decrypt and send you decrypted files for free.
* Please note that files must not contain any valuable information and their total size must be less than 5Mb.
Please don't worry, we can help you to RESTORE your server to original
state and decrypt all your files quickly and safely!
OUR HELP!
You have to pay for our help in Bitcoin Cryptocurrency.
Immidiately after payment we will send you (by e-mail) automatic decryption tool and your unique decryption key. You just have to start decryption tool on your server and all files will be automatically decrypted. All original file names will be restored too.
Moreover, DECP ransomware changes your background image, to make sure, that you have read the message. This image doesn’t provide any new information, it’s just a summary of a previous file.
It’s a great risk to trust them with your money without any firm guarantee. You can easily be deceived as they don’t have to stick to their words as there is no reason to help you. That’s why we advise to avoid any contact with the ransoms. If you need to remove DECP ransomware and decrypt .DECP files badly, you may try our solutions for free!
Article’s Guide
- How to remove DECP Ransomware from your computer
- How to remove DECP Ransomware encryption from your files
- Data Recovery
- Automated decryption tools
- Windows Previous Versions
How to remove DECP Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove DECP from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like DECP, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt .[deccrypasia@yahoo.com].*random*.DECP files?
Once you’ve removed the virus, you are probably thinking how to decrypt .[deccrypasia@yahoo.com].*random*.DECP files. Let’s take a look at possible ways of decrypting your data.
Recover data with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Restore data with automated decryption tools
Unfortunately, due to the novelty of DECP ransomware, there are no available automatic decryptors for this encryptor yet. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Restore data with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore the system with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Was this tutorial helpful?[Total: 0 Average: 0]
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.


