What is Matrix Ransomware?
In this article, we will discuss in detail how to remove Matrix Ransomware and decrypt .[Kromber@tutanota.com] files. Matrix Ransomware is a rather old cryptovirus that appeared in the distant 2016. His activity was noticed in November 2016. Initially, the cryptovirus was aimed at users speaking in Russian and English, However, judging by the latest data, the cryptovirus has already spread almost throughout the world. .[Kromber@tutanota.com] is the latest variation of the extension that is added to the encrypted files. It is worth noting that, first of all, the cryptovirus encrypts the most common user data, such as audio files, video, multimedia, archives, and much more. Here is the latest note on the terms of the ransom from the intruders, which is created in each folder containing encrypted files:
#_#ReadMe#_#.rtf
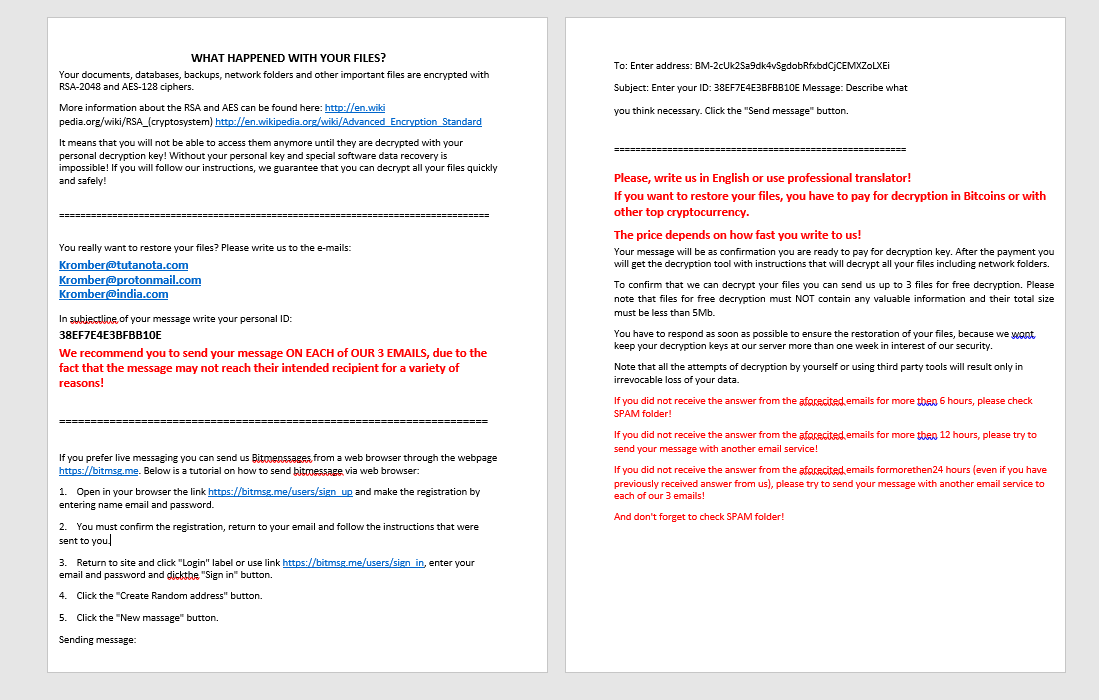
WHAT HAPPENED WITH YOUR FILES?
Your documents, databases, backups, network folders and other important files are encrypted with RSA-2048 and AES-128 ciphers.
More information about the RSA and AES can be found here: http://en.wiki pedia.org/wiki/RSA_(cryptosystem) http://en.wikipedia.org/wiki/Advanced_Encryption_Standard
It means that you will not be able to access them anymore until they are decrypted with your personal decryption key! Without your personal key and special software data recovery is impossible! If you will follow our instructions, we guarantee that you can decrypt all your files quickly and safely!
=================================================================================
You really want to restore your files? Please write us to the e-mails:
Kromber@tutanota.com
Kromber@protonmail.com
Kromber@india.com
In subjectline of your message write your personal ID:
38EF7E4E3BFBB10E
We recommend you to send your message ON EACH of OUR 3 EMAILS, due to the fact that the message may not reach their intended recipient for a variety of reasons!
====================================================================
If you prefer live messaging you can send us Bitmenssages from a web browser through the webpage https://bitmsg.me. Below is a tutorial on how to send bitmessage via web browser:
1. Open in your browser the link https://bitmsg.me/users/sign_up and make the registration by entering name email and password.
2. You must confirm the registration, return to your email and follow the instructions that were sent to you.
3. Return to site and click “Login” label or use link https://bitmsg.me/users/sign_in, enter your email and password and dickthe “Sign in” button.
4. Click the “Create Random address” button.
5. Click the “New massage” button.
Sending message:
To: Enter address: BM-2cUk2Sa9dk4vSgdobRfxbdCjCEMXZoLXEi
Subject: Enter your ID: 38EF7E4E3BFBB10E Message: Describe what you think necessary. Click the “Send message” button.
=======================================================
Please, write us in English or use professional translator!
If you want to restore your files, you have to pay for decryption in Bitcoins or with other top cryptocurrency.
The price depends on how fast you write to us!
Your message will be as confirmation you are ready to pay for decryption key. After the payment you will get the decryption tool with instructions that will decrypt all your files including network folders.
To confirm that we can decrypt your files you can send us up to 3 files for free decryption. Please note that files for free decryption must NOT contain any valuable information and their total size must be less than 5Mb.
You have to respond as soon as possible to ensure the restoration of your files, because we wont keep your decryption keys at our server more than one week in interest of our security.
Note that all the attempts of decryption by yourself or using third party tools will result only in irrevocable loss of your data.
If you did not receive the answer from the aforecited emails for more then 6 hours, please check SPAM folder!
If you did not receive the answer from the aforecited emails for more then 12 hours, please try to send your message with another email service!
If you did not receive the answer from the aforecited emails formorethen24 hours (even if you have previously received answer from us), please try to send your message with another email service to each of our 3 emails!
And don’t forget to check SPAM folder!
Over the past 3 years, the virus has constantly changed the file extension and notes with the terms of redemption. Here are the extensions that were used:
(note – files extension)
MATRIX-README.RTF – .matrix
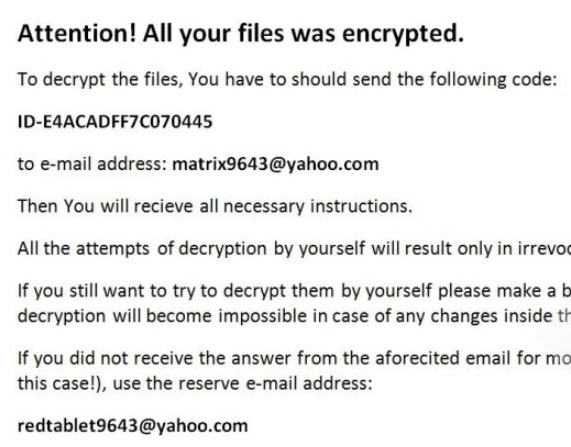
#_#RAD_README#_#.rtf – .RAD

lock screen – .enc
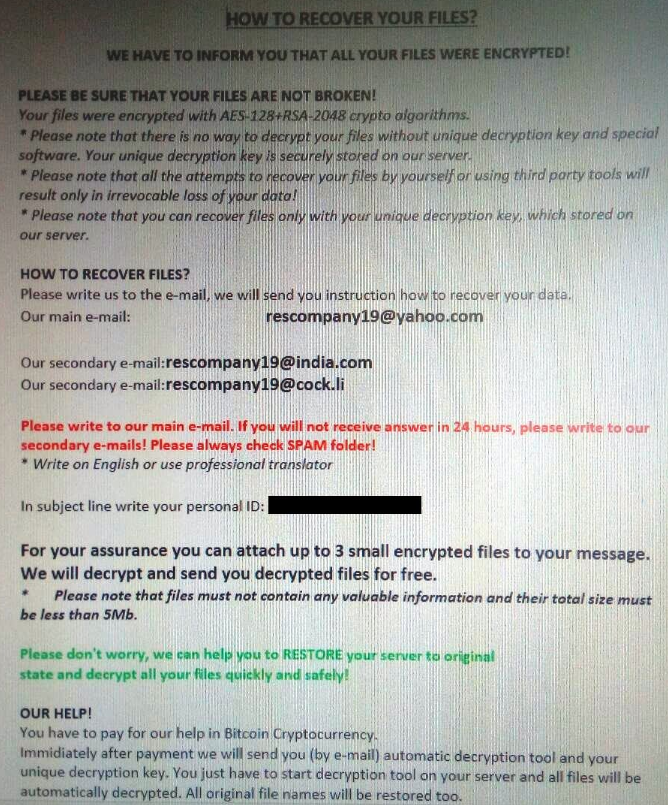
_!PEDANT_INFO!.rtf – .PEDANT
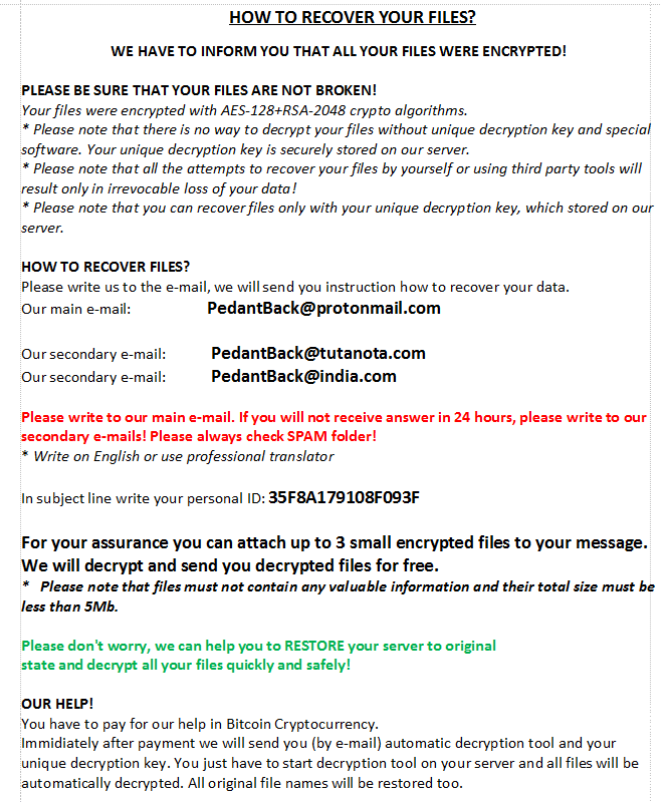
lock screen – .MDEN, .SDEN
lock screen – .CRYPTO
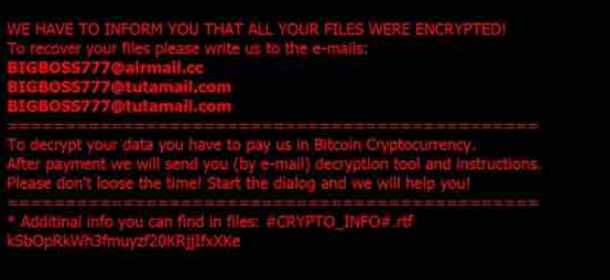
!README_ITLOCK!.rtf – .ITLOCK
lock screen – .SCR
!SBLOCK_INFO!.rtf – .SBLOCK
!GBLOCK_INFO.rtf – .GBLOCK
lock screen – .PLANT
!README_SPCT!.rtf – .SPCT
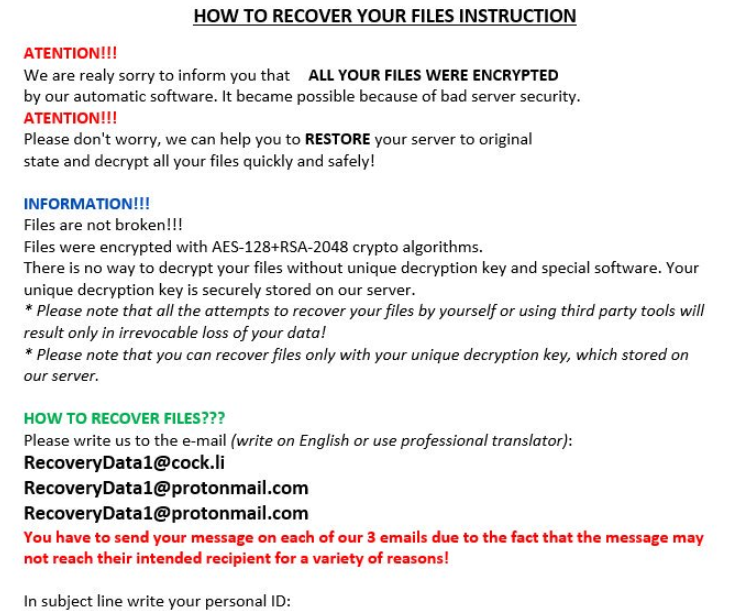
!README_GMBN!.rtf – .GMBN
and more
Malefactors demand payment of the ransom in the amount of several hundred dollars, namely it is necessary to pay in bitcoins. Also in the note are several e-mail addresses with which you can contact the attackers. Of course, we do not recommend you to pay, as there are no guarantees that your files will actually be where encrypted. Moreover, why spend money if you can try to remove it yourself. Use our recommendations to remove Matrix Ransomware and decrypt .[Kromber@tutanota.com] files.
Update: Use following service to identify the version and type of ransomware you were attacked by: ID Ransomware. If you want to decrypt your files, please follow our instruction below or, if you have any difficulties, please contact us: submit@securitystronghold.com. We really can help to decrypt your files.
How to remove Matrix from your computer?
You may try to use anti-malware tool to remove Matrix ransomware from your computer. Newly advanced ransomware detection technology is able to run an instant ransomware scan, which is perfect to protect your computer in case of a new ransomware attack.
SpyHunter provides an opportunity to remove 1 detected malware for free during trial period. The full version of the program costs $39,99 (you get 6 months of subscription). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
How to decrypt .Matrix files?
Once you’ve removed the virus, you are probably thinking of recovering files from encryption. Let’s take a look at possible ways of decrypting your data.
Recover data with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
Restore data with automated decryption tools
Unfortunately, due to the novelty of Matrix ransomware, there are no available automatic decryptors for this encryptor yet. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Restore data with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Matrix copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore the system with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Written by Rami D


 SpyHunter provides an opportunity to remove 1 detected malware for free during trial period. The full version of the program costs $39,99 (you get 6 months of subscription). By clicking the button you agree to
SpyHunter provides an opportunity to remove 1 detected malware for free during trial period. The full version of the program costs $39,99 (you get 6 months of subscription). By clicking the button you agree to