What is NW24 Ransomware?
NW24 Ransomware is a ransomware crypto-virus that encrypts user data in various formats, including photos, videos, archives, text documents, and much more. Of course, such data is extremely important for users and they are ready to do almost anything to get it back. This is the main target of the attackers.
The virus belongs to a large family of crypto viruses known as Dharma. The first activity of this virus was detected at the end of August 2020 and in just a few days it spread throughout the world, although it was originally targeted at English-speaking users.
In addition, NW24 Ransomware gives files a new .nw24 extension, which makes them permanently inoperable. Moreover, it is impossible to edit them manually. Also, the virus creates informants that contain information about encryption and ransom methods.
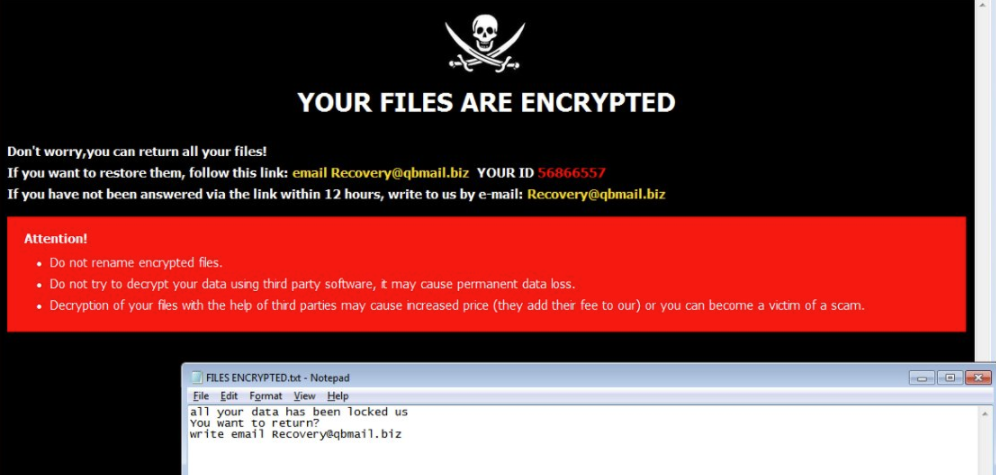
FILES ENCRYPTED.txtYOUR FILES ARE ENCRYPTED
Don’t worry,you can return all your files!
If you want to restore them, follow this link:email newhelper24@protonmail.ch YOUR ID –
If you have not been answered via the link within 12 hours, write to us by e-mail:newhelper@cock.li
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
all your data has been locked us
You want to return?
write email newhelper24@protonmail.ch or newhelper@cock.li
The scammers are demanding a ransom of an unspecified amount. According to our data, the amount can reach several thousand dollars. Moreover, no one can guarantee you that cybercriminals will actually provide you with the decryption key, even if you fully comply with their requirements. We do not recommend you pay, use our recommendations to remove NW24 Ransomware and decrypt .nw24 files.
Article’s Guide
- How to remove NW24 ransomware from your computer
- Automatically remove NW24 ransomware
- Manually remove NW24 ransomware
- How to decrypt .NW24 files
- Automatically decrypt .NW24 files
- Manually decrypt .NW24 files
- How to prevent ransomware attacks
- Remove NW24 ransomware and decrypt .NW24 files with our help
How to remove NW24 ransomware from your computer?
Every day ransomware viruses change as well as their folders, executable files and the processes, which they use. For this reason it’s difficult to detect the virus yourself. That’s why we’ve prepared the detailed guide for you on how to remove NW24 ransomware from your computer!
Automatically remove NW24 ransomware
We strongly recommend you to use automated solution, as it can scan all the hard drive, ongoing processes and registry keys. It will mitigate the risks of the wrong installation and will definitely remove NW24 ransomware from your computer with all of its leftovers and register files. Moreover, it will protect your computer from future attacks.
Our choice is Norton 360 . Norton 360 scans your computer and detects various threats like NW24 virus, then removes it with all of the related malicious files, folders and malicious registry keys. Moreover, it has a great variety of other features, like protection from specific ransomware attacks, safe box for your passwords and many other things!

Manually remove NW24 ransomware
This way is not recommended, as it requires strong skills. We don’t bear any responsibility for your actions. We also warn you that you can damage your operating system or data. However, it can be a suitable solution for you.
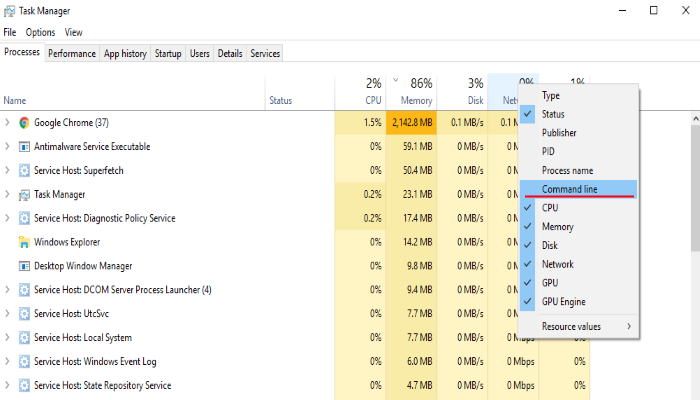
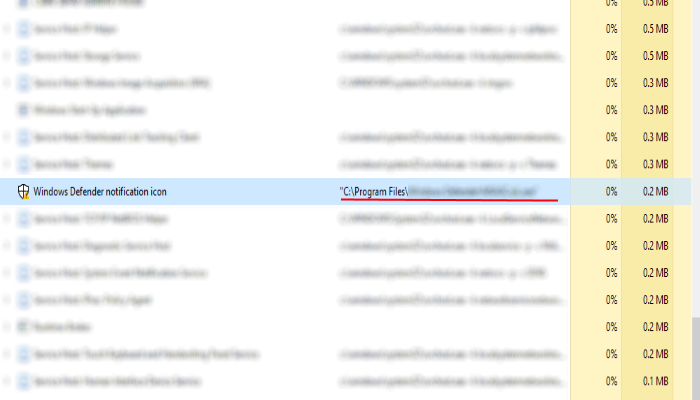
- Open the “Task Manager”
- Right click on the “Name” column, add the “Command line”
- Find a strange process, the folder of which probably is not suitable for it
- Go To the process folder and remove all files
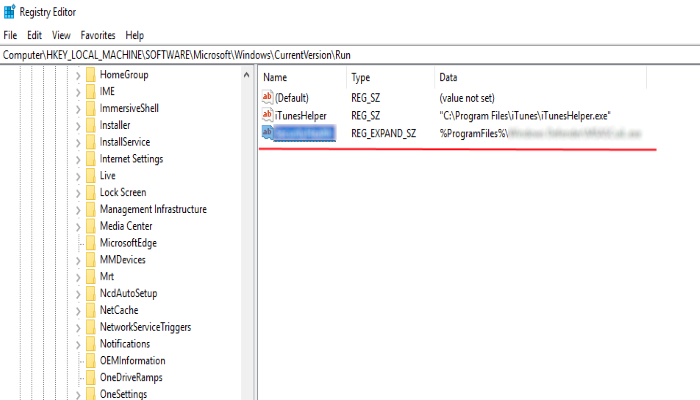
- Go to the Registry and remove all keys related to the process
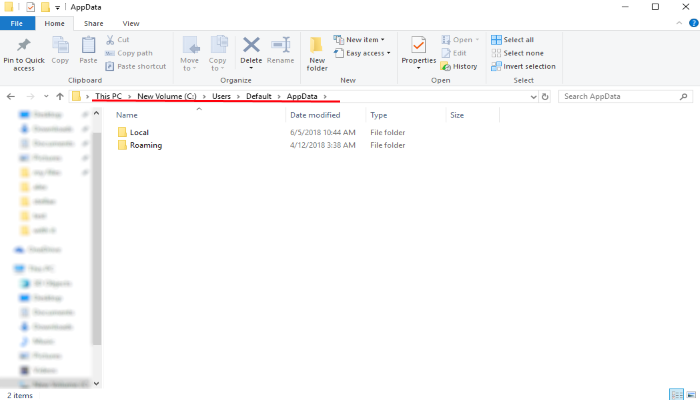
- Go to the AppData folder and remove all strange folders, that you can find
How to decrypt .NW24 files?
Restore .NW24 files with Stellar Data Recovery
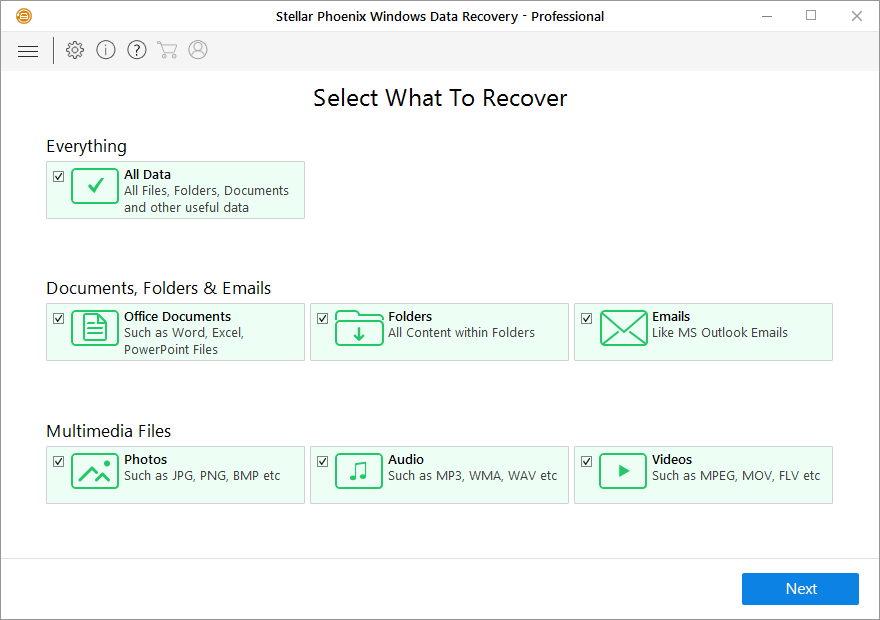

- Download and install Stellar Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
Other solutions
The services we’ve mentioned in this part also guarantee users, that the encrypted data is unlikely to become damaged. But you should understand, that there is still a risk to corrupt your files.
Decrypt .NW24 files with Emsisoft decryptor
Decrypt .NW24 files with Kaspersky decryptors
Decrypt .NW24 files with Dr. Web decryptors
Decrypt .NW24 files manually
If above mentioned solutions didn’t help to decrypt .NW24 files, still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Restore .NW24 files with Windows Previous Versions
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore .NW24 files with System Restore
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
How to prevent ransomware attacks?
If you have successfully removed NW24 ransomware, you know probably think about the ways how to protect your data from future attacks. The best way is to create backups of your data. We recommend you to use only high-quality products. Our choice here is Stellar Data Recovery. This soft can easily create highly-qualified backups, has a user-friendly interface and moreover, it can help you to restore your files! Then you should take strict control of all your internet connections. Some of the ransomware viruses connect to various internet services and can even infect computers that are connected to the same local network.
CONCLUSION: nowadays, these solutions are all possible ways to remove NW24 ransomware and decrypt “.NW24” files. Nowadays the best way to remove it is the Norton 360 . Their specialists improve the scanning system and update the databases every day. It helps not only to remove existing problems but also protects computers from future attacks. If there is a new way to decrypt your files, we will update the article, so stay tuned.