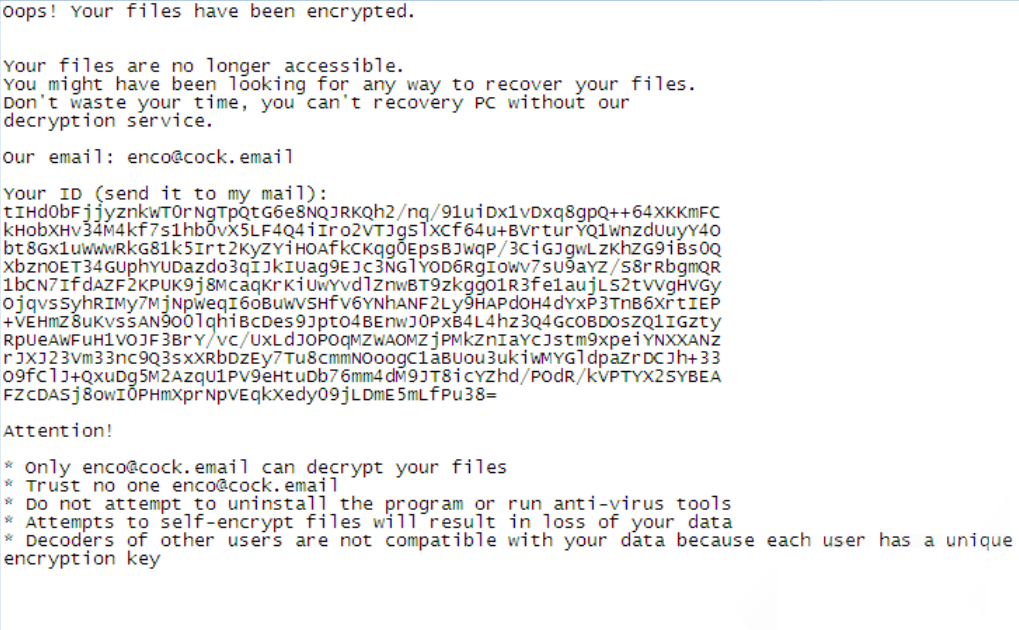
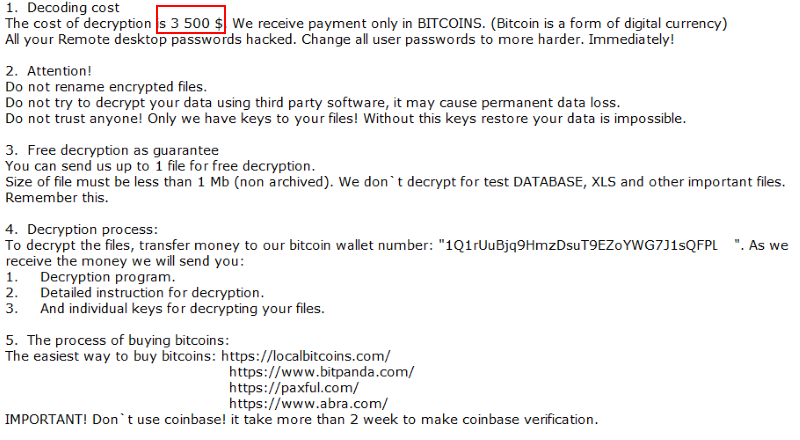
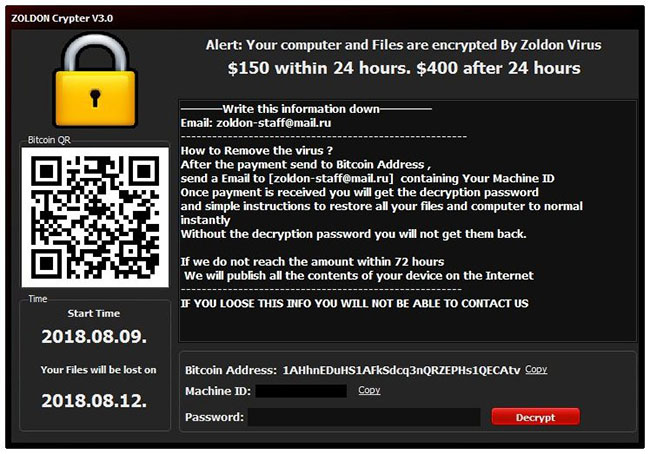
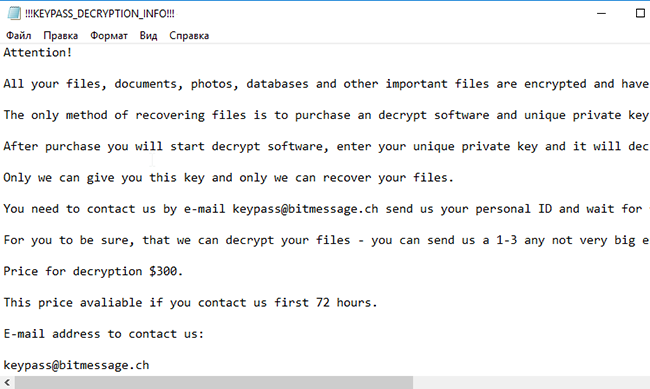
How to remove ONI Ransomware and restore .ONI files
ONI ransomware is a new virus, that is actively spreading around the internet. We strongly recommend to any user no to open suspicious attachments from spam emails. A proper anti-virus application will help too, as consequences of ransomware viruses are quite disastrous. If ONI somehow managed to get into a victim’s computer, it will immediately run encryption procedure with AES encryption algorithm to encode victim’s sensitive and vulnerable files (documents of any type, images, videos). ONI ransomware will completely rename files’ names with random characters and numbers and add .ONI extension. This tutorial will help you to remove ONI ransomware and decrypt .ONI files.