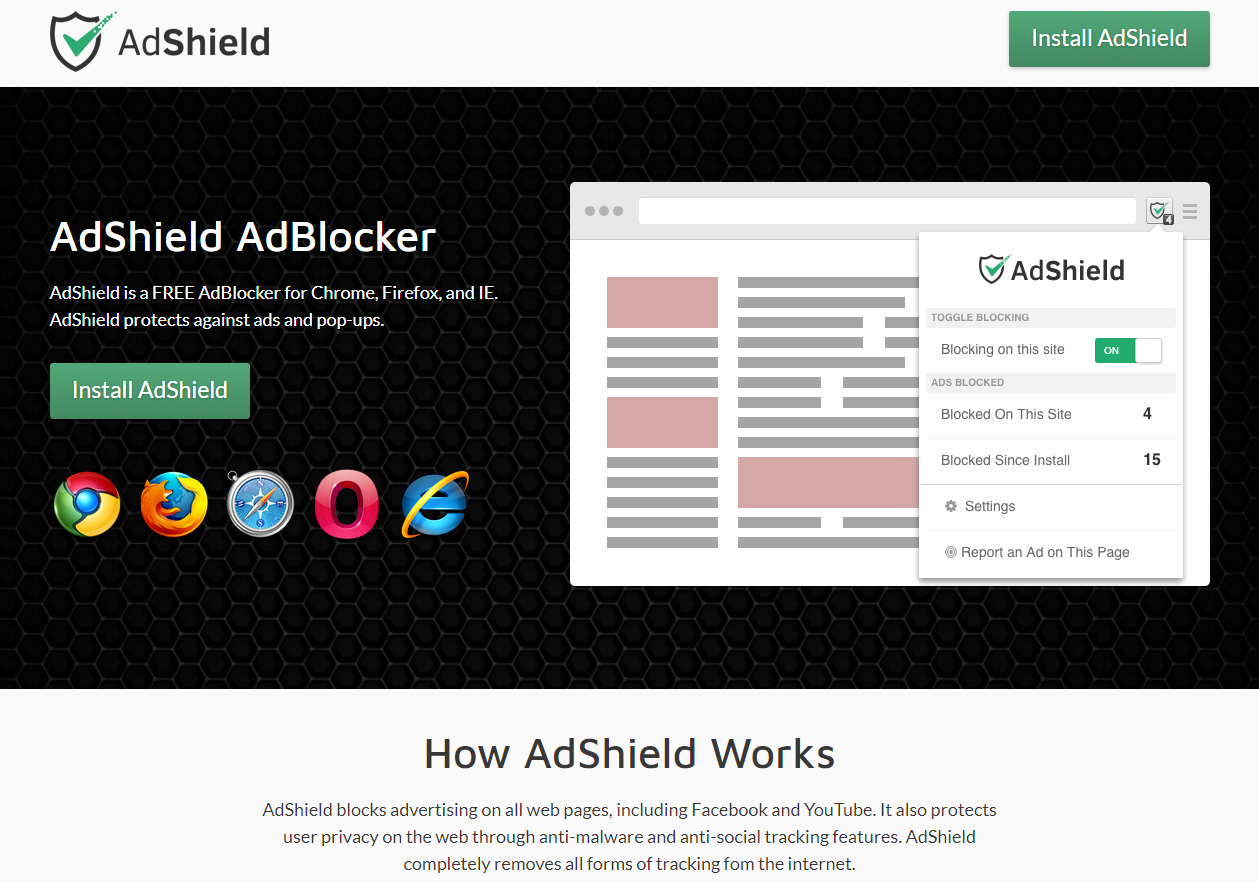
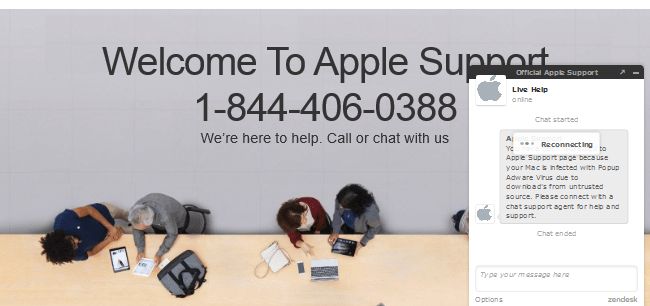
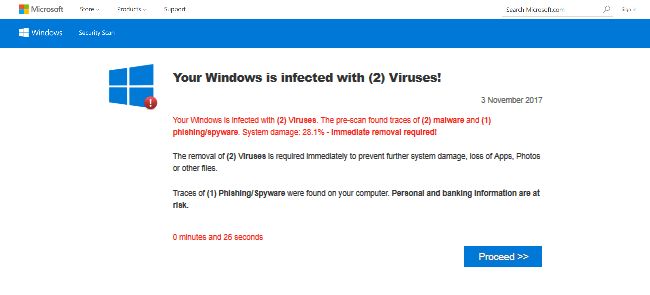
How to remove AdShield
AdShield may have a look of a legit extension, but you should know that PC security experts categorize this application as a browser hijacker. AdShield will get your browser configurations changed without your permission and disrupt your browsing experience with constant advertisement sponsored by third-party companies. That’s why we advise you to remove AdShield browser extension.