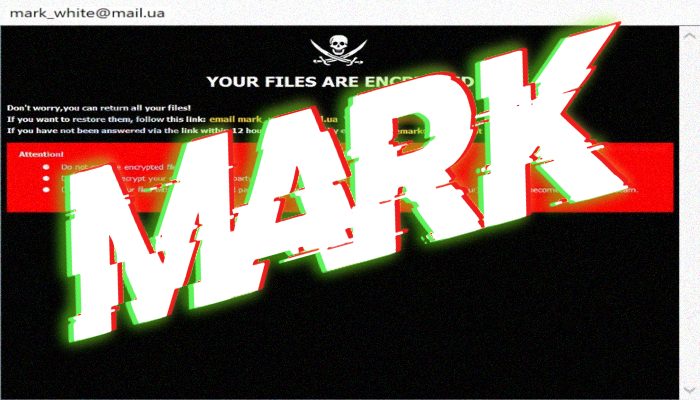
How to remove EIGHT ransomware and decrypt “.EIGHT” files
What is EIGHT? If you faced that the extensions of your files have been changed to “.id[*random*].[use_harrd@protonmail.com].EIGHT“, it means that your computer is infected with EIGHT ransomware. This virus belongs to the Phobos file-encryption ransomware family, whose members are Dewar, Calum, cmdrootairmail Money, admincrypt Money, adminstex777 Money, Oo7 and CASH ransomwares. Nowadays, this family is … Read more