How to remove Horse Ransomware and decrypt .horse files
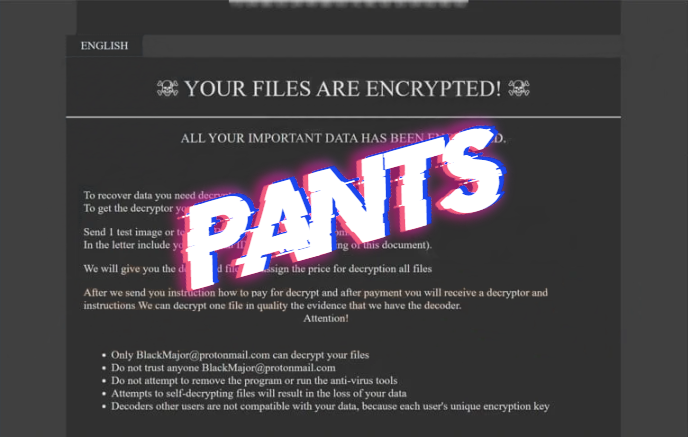
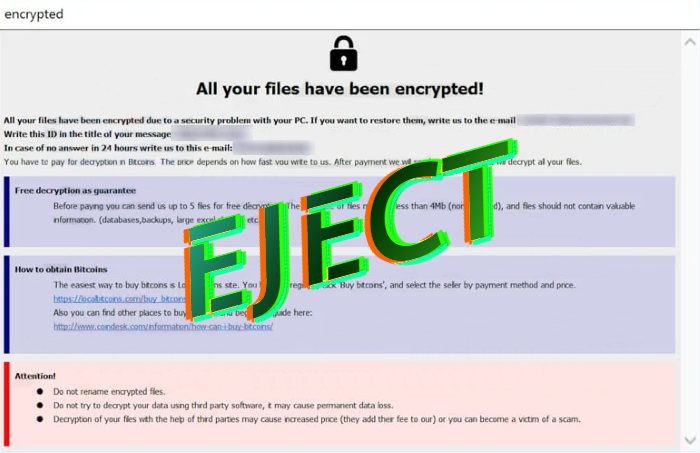
What is Horse Ransomware? Horse ransomware is one of the most dangerous viruses, namely ransomware. Moreover, genealogically, it belongs to the Phobos family, which has spread very much throughout the world in recent months. Cybercriminals only change the content, but the goal remains the same – to make the user pay. Horse ransomware encrypts data … Read more