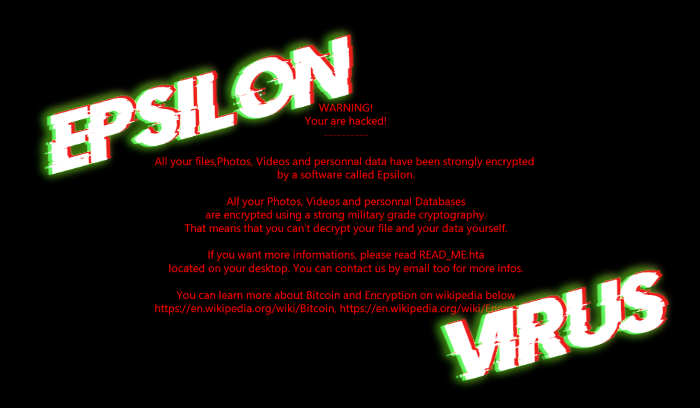
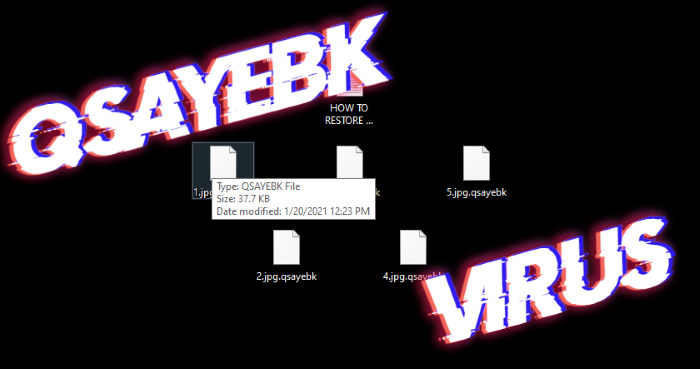
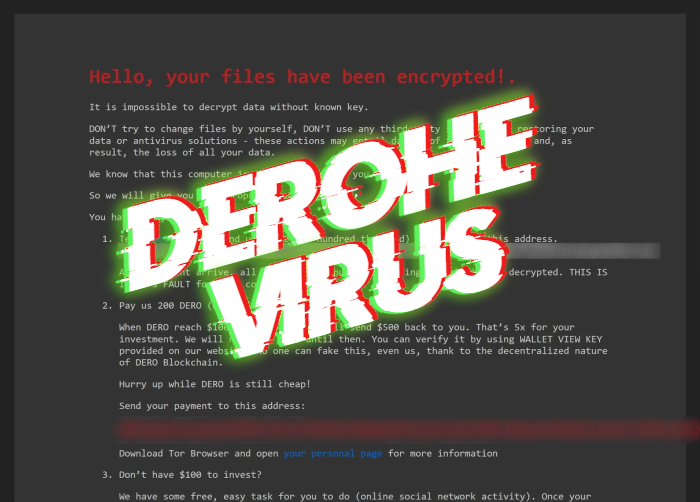
Remove LTC ransomware and decrypt “.[leeza@keemail.me].LTC” files
What does “.[leeza@keemail.me].LTC” extension mean? Unfortunately, if to the extension of your files have been added “.[leeza@keemail.me].LTC” one, your computer is infected with LTC ransomware. We refer this virus to Dharma file-encryption ransomware family. Mainly, such viruses spreads by the means of malicious executable files, which are promoted as installers. In our case, we’ve got … Read more