Article’s Guide
- What does .RDP stand for?
- RDP ransomware encryption process.
- How to remove RDP Ransomware from your computer
- How to decrypt .RDP files
- Data Recovery
- Automated decryption tools
- Other software
What does .RDP stand for?
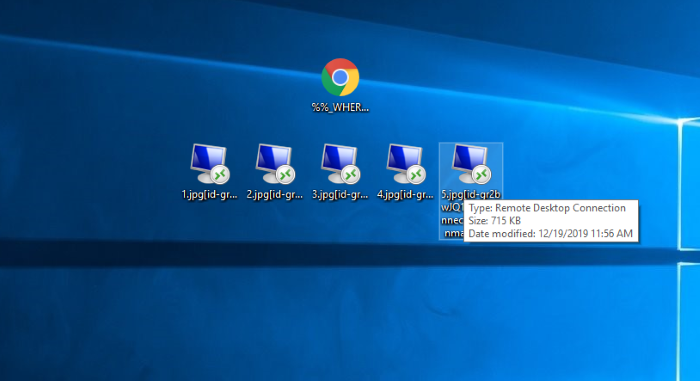
A few days ago malware research specialists have found new threat, that is called RDP ransomware. This virus prevents the victims from the accessing to files by modifying their structures. The clearest sign of the infection with this virus is [id-*unique*].[rdpconnect@protonmail.com].RDP extension. Files gets this extension after the encryption process. Nowadays, hackers use various ways to infect the device. The one of the newest is the compromised ScreenConnect. Once this software has been installed, the client called ScreenConnect.ClientService.exe begins to work in the background waiting for the remote commands. By the means of this soft the criminals can easily get the full control upon your device. Moreover, RDP ransomware can be injected into installators, be sent by email and etc. That’s why it’s necessary to be attentive on the internet. If your computer is already infected with this virus, we should warn you not to try to remove RDP ransomware and decrypt .RDP files manually. Every manual changing of the file can easily damage it without a hope to restore it.
RDP ransomware encryption process.
Once RDP ransomware has been installed, it immediately begins to prepare system and files for the encryption process. At first the virus scans the hard drive. It searches for the files that can be encrypted. In the most cases RDP ransomware can encrypt only media files, documents, databases and etc. However, it can be easily modified and get the ability to damage system files or even lock the hard drive. When the files are found, RDP ransomware immediately begins to modify their structures. As the result the files are unreadable and get the new extension – [id-*unique*].[rdpconnect@protonmail.com].RDP, that is added to the files’ names. The purpose of this attack is to force the victim to pay a ransom for the decryption services, that hackers offer. That’s why the virus creates the ransom note, that is called %%_WHERE_MY_FILES_=#.html. We strongly recommend you to avoid any contact with them, as it can potentially lead to a greater problem, than encryption. It’s not a unique situation, when hackers just stop all the contacts with the victims once they’ve been paid. Moreover, sometimes they just destroy all the information on the hard drive or infect with a virus. So you’d better think twice before you decide. Especially for this case we’ve prepared the guide on how to remove RDP ransomware and decrypt .RDP files! Here we’ve enumerated all possible ways to remove RDP virus and to decrypt .RDP files.
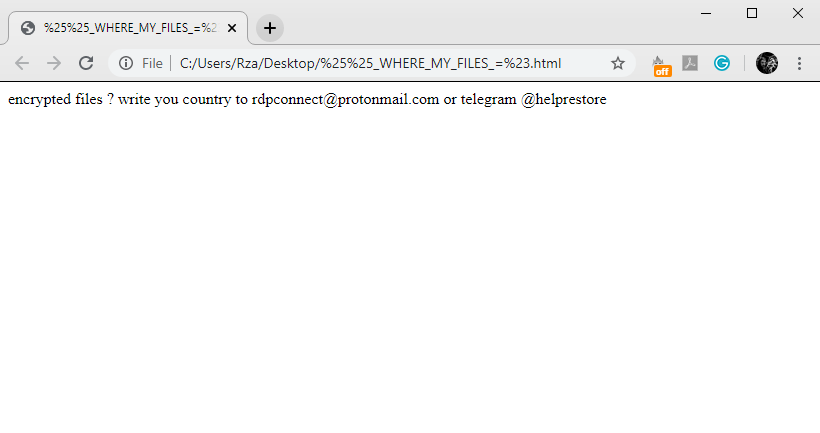
%%_WHERE_MY_FILES_=#.html
rdpconnect@protonmail.com or telegram
@helprestore
How to remove RDP Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove RDP from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like RDP, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt “.RDP” files?
Once you’ve removed the virus, you are probably thinking how to decrypt “.RDP” files or at least restore them. Let’s take a look at possible ways of decrypting your data.
Restore “.RDP” files with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Decrypt “.RDP” files with other software
Unfortunately, due to the novelty of RDP ransomware, there are no decryptors that can surely decrypt encrypted files. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Decrypt .RDP files with Emsisoft decryptor
This software includes information about more than 100 viruses of STOP(DJVU) family and others. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.
Restore .RDP files with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore .RDP files with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Was this tutorial helpful?[Total: 0 Average: 0]
This software includes information about more than 100 viruses of STOP(DJVU) family and others. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore .RDP files with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Was this tutorial helpful?[Total: 0 Average: 0]
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.