Odveta ransomware encryption process
The freshly made internet threat, that can possibly infect every computer, is called Odveta ransomware. This virus belongs to the Ouroboros file-encryption ransomware family and has the same principles of work like representatives of STOP(DJVU) family: Nols, Werd, Ndarod, Leto, Bora; and Dhrama family: Money, Oo7 and CASH. The viruses that can be classified as ransomwares modify the files with the aim to make them unreadable by the operating system. One of the ways of disseminating of Odveta ransomware is email attachments. The malicious code is put into a harmless file and once a recepient of the messages decides to open it, the code activates and sneaks into the system. It’s very easy to understand, that your device has been infected with this virus, and if it’s so, you’d better not to try to remove Odveta encryption manually. Every manipulation with the file can possibly corrupt it.
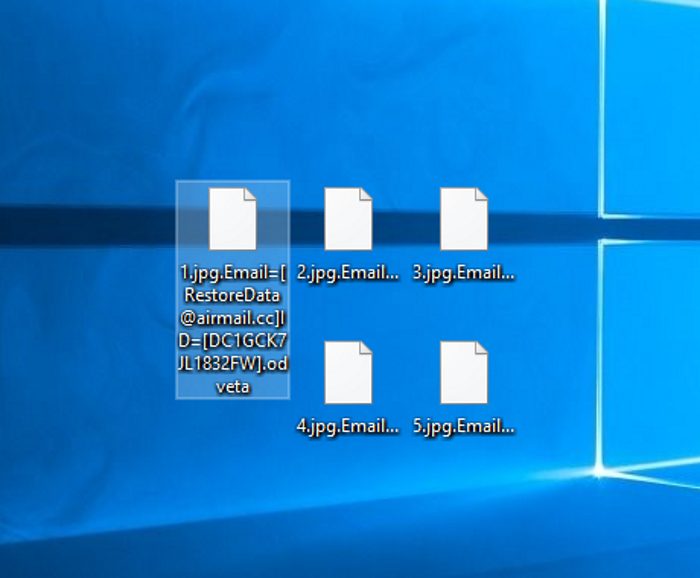
The Odveta ransomware encryption process can be described as a two-step process. The encryption process is initiated by a search for the relevant files on the basis of suitableness for the encryption. The desired files are media files of different formats and all types of documents. Odveta ransomware scans all the folders on the hard drive and connected devices. When it’s done, the virus initiates modification process that occures according to the unique algorithm. After it the operating system in unanable to read these files, that are marked with the new extension .Email=[RestoreData@airmail.cc]ID=[*random*].odveta. The main purpose of this attack is to force the owner of the infected device to pay for the decryption service, that hackers offer. That’s why the virus also create the ransom note, that is called Unlock-Files.txt and contains the following information:
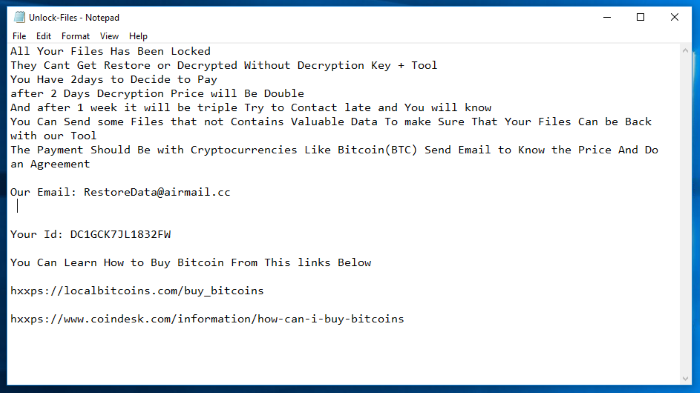
All Your Files Has Been Locked
You Have 2days to Decide to Pay
after 2 Days Decryption Price will Be Double
And after 1 week it will be triple Try to Contact late and You will know
You Can Send some Files that not Contains Valuable Data To make Sure That Your Files Can be Back with our Tool
The Payment Should Be with Cryptocurrencies Like Bitcoin(BTC) Send Email to Know the Price And Do an Agreement
Our Email: RestoreData@airmail.cc
Your Id: *random*
You Can Learn How to Buy Bitcoin From This links Below
hxxps://localbitcoins.com/buy_bitcoins
hxxps://www.coindesk.com/information/how-can-i-buy-bitcoins
The words of the criminals cannot be trusted. There is a great risk of being deceived, as there is no any firm guarantee, that hacker will honor their promises. We strongly recommend you to avoid any contact with the ransom, as they can make the situation even worse. After the payment you can get a more malicious malware instead of a decryption tool, moreover, you can become a victim of their new ransomware. That’s why we provide you with a guide on how to remove Odveta ransomware and decrypt .odveta files for free!
Article’s Guide
- How to remove Odveta Ransomware from your computer
- How to remove Odveta Ransomware encryption from your files
- Data Recovery
- Automated decryption tools
- Windows Previous Versions
How to remove Odveta Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove Odveta from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like Odveta, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt .Email=[RestoreData@airmail.cc]ID=[*random*].odveta files?
Once you’ve removed the virus, you are probably thinking how to decrypt .Email=[RestoreData@airmail.cc]ID=[*random*].odveta files. Let’s take a look at possible ways of decrypting your data.
Recover data with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Restore data with automated decryption tools
Unfortunately, due to the novelty of Odveta ransomware, there are no available automatic decryptors for this encryptor yet. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Remove Odveta with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Remove Odveta with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Was this tutorial helpful?[Total: 0 Average: 0]
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.


