What is Kirk Ransomware?
Kirk Ransomware is a fresh virus that encrypts your personal files, therefore making them unavailable to user. Once infiltrated, Kirk Ransomware starts to search for such types of data like photos, documents, video, and so on. Then, the encryption process is started which takes a little time so the user may not even notice anything suspicious. After completion of the process, file extension of your files will be appended with the “.kirked”. For example, myfamily.jpg file turns into myfamilyKirk.kirked file. Then you will see a pop-up window containing ransom message. It also creates a text file (“RANSOM_NOTE.txt”) which it places on the desktop.
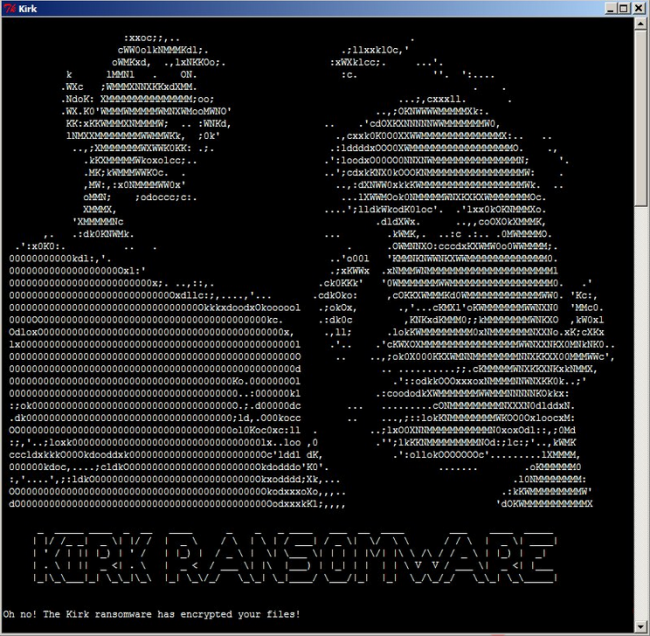
Here is used a typical scheme of all ransomware-type viruses – to force victim to pay them. The only differences of them are the ransom price and encryption method. Cyber criminals state that there are no ways to recover your files but to pay ransom. Once payment is done, they will supposedly send you decryption key. But you should know that nobody can guarantee that they will fulfill their end of the bargain. The practice shows that they are just ignoring people who pays them. That’s why you should not be pushed about by them because you can remain without money and files. On the contrary, you only may encourage them to continue their dirty business. In any case, you will be simply scammed. In order to solve your problem, we prepared this step-by-step guide. First things first, you should remove Kirk ransomware as decryption procedure loses its meaning without this. The best solution to this is to use SpyHunter removal tool which contains Kirk ransomware in its database, so that it will completely wipe out virus from your computer.
Here’s information you can find in Kirk ransom notes:
Oh no! The Kirk ransomware has encrypted your files!
! IMPORTANT ! READ CAREFULLY: Your computer has fallen victim to the Kirk malware and important files have been encrypted – locked
up so they don’t work. This may have broken some software, including games, office suites etc. Here’s a list of some the file extensions that were targetted: .3g2, .rar, .jar, .cgi, .class, .jtd, .potx, .xex, .dds, .3gp, .jpg, .csv, .pl, .cd, .jtt, .potm, .tiger, .ff, .asf, .jpeg, .psd, .com, .java, .hwp, .sda, .lbf, .yrp, .asx, .png, .wav, .wsf, .swift, .602, .sdd, .cab, .pck, .avi, .tiff, .ogg, .bmp, .vb, .pdb, .sdp, .rx3, .t3, .flv, .zip, .wma, .bmp, .ods, .psw, .cgm, .epk, .ltx, .ai, .7z, .aif, .gif, .xlr, .xlw, .wotreplay.vol, .uasset, .m2ts, .dif.z, .mpa, .tif, .xls, .xlt, .rofl, .asset, .bikey, .mkv, .exe .wpl, .tiff, .xlsx, .xlsm, .pak, .forge, .patch, .mov, .tar.gz, .arj, .htm, .dot, .xltx, .big, .lng, .upk, .mp4, .tar, .deb, .js .docm, .xltm, .bik .sii, .uax, .mpg, .mp3, .pkg, .jsp, .dotx, .xlsb, .xtbl, .litemod, .mdl, .mpeg, .sh, .db, .php, .dotm, .wk1, .unity3d, .vef, .lvl, mpeg4, .c, .dbf, .xhtml, .wpd, .wks, .capx, .dat, .qst, .rm, .cpp, .sav, .cfm, .wps, .123, .ttarch, .papa, .ddv, .swf, .h, .xml, .rss, .rtf, .sdc, .iwi, .psark, .pta, .vob, .mov, .html, .key, sdw, .slk, .rgss3a, .ydk, .wmv, .gif, .aiml, .odp, .sgl, .pxl, .gblorb, .mpq, .doc, .txt, .apk, .pps, .vor, .wb2, .xwm, .wtf, .docx, .py, .bat .ppt, .uot, .pot, .j2e, .bsa, .pdf, .pyc, .bin, .pptx, .uof, .pptm, .mpk, .re4 There are an additional 441 file extensions that are targetted. They are mostly to do with games. To get your files back, you need to pay. Now. Payments recieved more than 48 hours after the time of infection will be charged double. Further time penalties are listed below. The time of infection has been logged. Any files with the extensions listed above will now have the extra extension ‘.kirked’, these files are encrypted using military grade encryption. In the place you ran this program from, you should find a note (named RANSOM_NOTE.txt) similar to this one. You will also find a file named ‘pwd’ – this is your encrypted password file. Although it was generated by your computer, you have no way of ever decrypting it. This is due to the security of both the way it was generated and the way it was encrypted. Your files were encrypted using this password. “Logic, mother******.” ~ Spock.
Decrypting your files is easy. Take a deep breath and follow the steps below.
1 ) Make the proper payment. Payments are made in Monero. This is a crypto-currency, like bitcoin. You can buy Monero, and send it, from the same places you can any other crypto-currency. If you’re still unsure, google ‘bitcoin exchange’. Sign up at one of these exchange sites and send the payment to the address below. Make note of the payment / transaction ID, or make one up if you have the option. Payment Address (Monero Wallet): 4AqSwfTexbNaHcn8giSJw3KPiWYHGBaCF9bdgPxvHbd5A8Q3Fc7n6FQCReEns8uEg8j… …Uo4BeB79rwf4XSfQPVL1SKdVp2jz Note: In 31 days your password decryption key gets permanently deleted. You then have no way to ever retrieve your files. So pay now.
2 ) Email us. Send your pwd file as an email attachment to one of the email addresses below. Include the payment ID from step 1. Active email addresses: kirk.help@scryptmail.com kirk.payments@scryptmail.com
3 ) Decrypt your files. You will recieve your decrypted password file and a program called ‘Spock’.
Download these both to the same place and run Spock. Spock reads in your decrypted password file and uses it to decrypt all of the
affected files on your computer. > IMPORTANT ! The password is unique to this infection. Using an old password or one from another machine will result in corrupted files. Corrupted files cannot be retrieved.
Don’t f*** around.
4 ) Breathe.
How Kirk infects your PC?
Like any other ransomware-type viruses, Kirk is distributed primarily through the fraudulent email messages. For example, it might be bill from tax company or online store like Amazon. The virus itself is hided within an attachment. Therefore, be very wary when opening files downloaded from suspicious emails or untrusted sources. Do not rush in these moments since you can compromise your system. The malware is also distributed through fake software updates, torrent (P2P) networks, and trojans as well.
To prevent suсh kinds of the threats as Kirk ransomware in the future follow these tips:
- Adjust your email anti-spam settings to filter out all potentially unsafe incoming messages.
- Make sure, the attachments with the following extensions: .js, .vbs, .docm, .hta, .exe, .cmd, .scr, and .bat. are in the black list
- Rename the vssadmin.exe process to protect Shadow Volume Copies of your files from removal.
- Raise the level of Firewall protection. It can prevent ransomware from connecting with its server.
- Do not forget to backup your files regularly. This will facilitate process of decrypting files in case of infection.
- Install antimalware tool because in most cases, it can detect ransomware in advance and remove the malware before the infection.
How to remove Kirk from your computer?
The best and easiest way to remove Kirk from your computer is to use special anti-malware program that has this threat in its database. As stated above, you need proper and reliable anti-malware program, that’s why we recommend you to use SpyHunter.
It scans your computer and detects various threats like Kirk, then completely removes it. One of the best features of this program – large threat’s database. SpyHunter’s newly advanced ransomware detection technology is able to run an instant ransomware scan and show you a message about detection. After deep scanning of your system, it will easily find and delete Kirk. Use this removal tool to get rid of Kirk for FREE.
How to decrypt .kirked files?
Once you’ve removed virus, you are probably thinking of recovering files from encryption. Let’s take a look at possible ways of decrypting your data.
Recover data with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
Decrypt encrypted files manually
You can try to use one of these methods in order to restore your encrypted data manually.
Restore data with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows saves copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore the system with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.


