What is ETH ransomware?
ETH ransomware is the newest virus from Dharma ransomware family. ETH ransomware can block all the personal files on your computer and makes it unreadable. First ETH infiltrates your system, then starts encoding procedure with AES encryption algorithm. Business/work documents, personal photos and videos – all of it may be enciphered, so that no one can use these files until they pay ransom cost, which is usually a big sum of money. In this article you can learn how to remove ETH ransomware and decrypt .ETH files.

When all user’s sensitive data is enciphered, it becomes inaccessible. ETH ransomware adds .ETH extension to the name of all the encrypted files. When all the data is encoded, the ransomware will drop FILES ENCRYPTED.txt file and display pop-up window with criminals’ demands. Here is ETH ransom note:
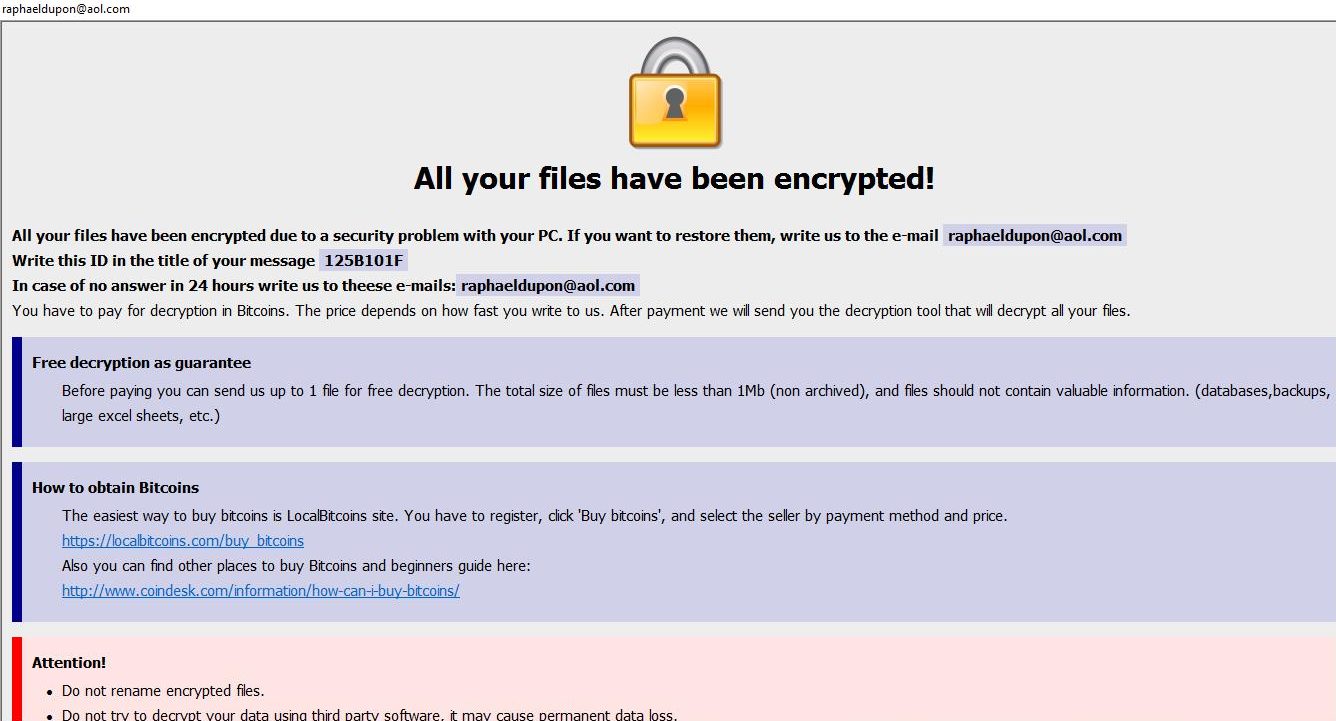
ETH is a typical ransomware, its main purpose is to force you to pay them. After finishing encrypting process, the ransomware will state that there are no ways to recover your files but to pay ransom. Cyber criminals demand ransom in BitCoins. Once you’ve done payment, they are suppose to send you decryption key. But you should know that cyber criminals are not going to give you a decryption key. Mostly they are just ignoring their victims. That’s why there is no need to contact them, it wouldn’t help. Still, ETH ransomware does very complicated encryption, but it does not damage, move or delete your files, which means you have chance to restore your personal data.
How to remove ETH ransomware from your computer and restore files?
You may try to use anti-malware tool to remove ETH ransomware from your computer. Newly advanced ransomware detection technology is able to run an instant ransomware scan, which is perfect to protect your computer in case of a new ransomware attack.
SpyHunter provides an opportunity to remove 1 detected malware for free during trial period. The full version of the program costs $39,99 (you get 6 months of subscription). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
How to decryptfiles encrypted by ETH?
Once you’ve removed virus, you are probably thinking of recovering files from encryption. Let’s take a look at possible ways of decrypting your data.
Decrypt ETH files with automated decryption tools
Unfortunately, due to novelty of ETH ransomware, there are no available automatic decryptors for this virus yet. Still, there is no need to invest in malicious scheme by paying ransom. You are able to recover files manually.
Decrypt ETH files manually
You can try to use one of these methods in order to restore your encrypted data manually.
Restore data with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows saves copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore the system with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Restore data with Shadow Explorer
Shadow Explorer is an application that is able to provide you with Shadow Copies created by the Windows Volume Shadow Copy Service.
- Once you’ve downloaded this application, open a folder with it;
- Right-click on the file ShadowExplorer-0.9-portable and choose Extract all option;
- Run ShadowExplorerPortable.exe;
- Look at the left corner, there you can choose desired hard drive and latest restore option;
- On the right side you can see the list of files. Choose any file, right-click on it and select Export option.
Restore data with Recuva
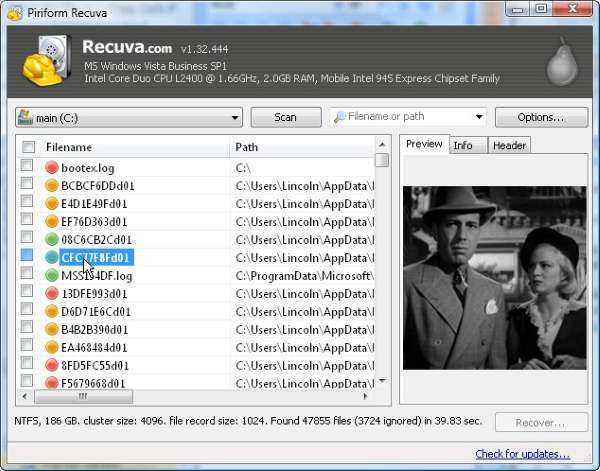
Recuva is a data recovery program for Windows, developed by Piriform. It is able to recover files that have been “permanently” deleted and marked by the operating system as free space.
- Once you’ve downloaded and installed this application, start it in Wizard mode: choose the Options button and then select Run Wizard;
- You will see Welcome to the Recuva Wizard page, choose Next;
- Open the File Type page and choose the type of data you need to recover, after select Next. If you don’t know what kind of data you are looking for, choose Other option;
- Choose the location of a search in the File Location window;
- In the Thank you window, select Start. After finishing searching process, Recuva will show you the results of search;
- Before recovering of the data, choose the Check Boxes near the file. You can see three types of colored dots. Green dot means that your chance to restore file is excellent. Orange one – chance to restore file is acceptable. And the red one shows you that it’s unlikely to happen;
- Select Recover option and choose the directory of the restored data.
How to protect PC from ETH?
It’s pretty difficult task to get rid of any ransomware, including ETH. But you can easily prevent any infection of your PC. HitmanPro.Alert’s CryptoGuard can help you with this problem. It’s one of the best anti-ransomware applications. No matter how sneaky it is, HitmanPro.Alert’s CryptoGuard will stop ETH infiltration to your system. After detection, this program removes all the related to the ransomware data and prevents your file from being encrypted.

 SpyHunter provides an opportunity to remove 1 detected malware for free during trial period. The full version of the program costs $39,99 (you get 6 months of subscription). By clicking the button you agree to
SpyHunter provides an opportunity to remove 1 detected malware for free during trial period. The full version of the program costs $39,99 (you get 6 months of subscription). By clicking the button you agree to