What is Ako?
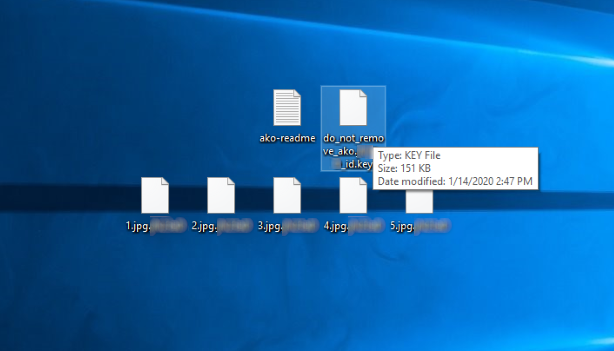
Ako is the newest file-encryption ransomware virus, the main function of which is to prevent an access to the definite file formats. The choice of the formats is the unique for every ransomware and in the case of infection with Ako ransomware it encrypts various media files and documents. We should mention the fact, that usually the creators of such viruses update them and add various new abilities, such as the increasing the number of formats that the virus can encrypt. As the rule Ako ransomware is spread by the means of various executable files (.exe). However, the malicious code can be easily injected into a usual document and be executed once such a file is opened. When Ako successfully injects into the operating system, it immediately begins to make changes in the Registry and your system in order to avoid detection by build-in protection system. Then it creates a number of files and tries to replace a common system process. Then it establishes the connection with a number of unknown IP addresses and begins the encryption process. Nowadays hackers not just encrypt files, but also steal valuable information, for the saving of privacy of which a victim should pay. The encryption itself can be subdivided into two parallel processes. Ako ransomware looks for the files, that are appropriate for encryption in all folders on the hard drive and modifies them. Encrypted files as the result get new extensions, which consist of victims’ ID numbers. Moreover, the virus creates the ransom note, that is called “ako-readme.txt” and the “do_not_remove_ako.*ID*_id.key” file. Unfortunately, the surest way to decrypt your files is to get the decryptor from hackers, as the encryption algorithms are unique for every computer. However, there is a great risk, that you will be just ignored by the criminals after your payment. Moreover, no one can guarantee you, that they won’t try to make the situation even worse. We recommend you to avoid any contact with them! However, there is still a hope: we’ve prepared the detailed guide on how to remove Ako ransomware and decrypt files, in which we’ve collected all possible ways to decrypt your files.
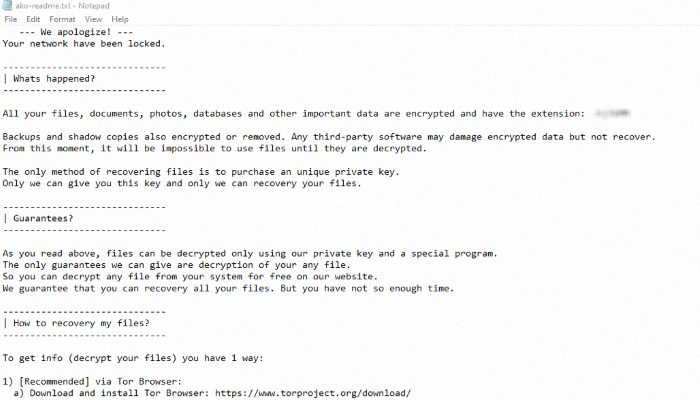
ako-readme.txt
All your files, documents, photos, databases and other important data are encrypted and have the extension: *ID*
Backups and shadow copies also encrypted or removed. Any third-party software may damage encrypted data but not recover.
From this moment, it will be impossible to use files until they are decrypted.
The only method of recovering files is to purchase an unique private key.
Only we can give you this key and only we can recovery your files.
To get info (decrypt your files) follow this steps:
1) Download and install Tor Browser: hxxps://www.torproject.org/download/
2) Open our website in TOR: hxxp://kwvhrdibgmmpkhkidrby4mccwqpds5za6uo2th cw5gz75qncv7rbhyad.onion/I8VC6PIEQL8JFKHM
3) Paste your ID in form (you can find your ID below)
!! ATTENTION !!
!! Any third - party software may damage encrypted data but not recover.
!! DO NOT MODIFY ENCRYPTED FILES
!! DO NOT CHANGE YOUR ID
!! DO NOT REMOVE YOUR ID.KEY FILE
--- BEGIN PERSONAL ID ---
*Key*
--- END PERSONAL ID ---
Article’s Guide
- How to remove Ako Ransomware from your computer
- How to decrypt Ako files
- Data Recovery
- Automated decryption tools
- Other software
How to remove Ako Ransomware from your computer?
We strongly recommend you to use a powerful anti-malware program that has this threat in its database. It will mitigate the risks of the wrong installation, and will remove Ako from your computer with all of its leftovers and register files.
Solution for Windows users: our choice is Norton 360 . Norton 360 scans your computer and detects various threats like Ako, then removes it with all of the related malicious files, folders and registry keys.
If you are Mac user, we advise you to use Combo Cleaner.
How to decrypt Ako files?
Once you’ve removed the virus, you are probably thinking how to decrypt Ako files or at least restore them. Let’s take a look at possible ways of decrypting your data.
Restore Ako files with Data Recovery

- Download and install Data Recovery
- Select drives and folders with your files, then click Scan.
- Choose all the files in a folder, then press on Restore button.
- Manage export location.
The download is an evaluation version for recovering files. To unlock all features and tools, purchase is required ($49.99-299). By clicking the button you agree to EULA and Privacy Policy. Downloading will start automatically.
Decrypt Ako files with other software
Unfortunately, due to the novelty of Ako ransomware, there are no decryptors that can surely decrypt encrypted files. Still, there is no need to invest in the malicious scheme by paying a ransom. You are able to recover files manually.
You can try to use one of these methods in order to restore your encrypted data manually.
Decrypt Ako files with Emsisoft decryptor
This software includes information about more than 100 viruses of STOP(DJVU) family and others. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.
Restore Ako files with Windows Previous Versions
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore Ako files with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Was this tutorial helpful?[Total: 0 Average: 0]
This software includes information about more than 100 viruses of STOP(DJVU) family and others. All that you need are two files or some luck. You can freely use it as it distributes free of charge. If it doesn’t work for you, you can use another method.
This feature is working on Windows Vista (not Home version), Windows 7 and later versions. Windows keeps copies of files and folders which you can use to restore data on your computer. In order to restore data from Windows Backup, take the following steps:
- Open My Computer and search for the folders you want to restore;
- Right-click on the folder and choose Restore previous versions option;
- The option will show you the list of all the previous copies of the folder;
- Select restore date and the option you need: Open, Copy and Restore.
Restore Ako files with System Restore
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.
Was this tutorial helpful?[Total: 0 Average: 0]
You can always try to use System Restore in order to roll back your system to its condition before infection infiltration. All the Windows versions include this option.
- Type restore in the Search tool;
- Click on the result;
- Choose restore point before the infection infiltration;
- Follow the on-screen instructions.